Imagine a scenario where a company’s sensitive financial information or proprietary information is at risk of being leaked. By implementing internal email policies and controlling email flow, businesses can prevent unauthorized external emails, ensuring that sensitive data remains secure within the organization.
Let’s take a look at the following scenario:
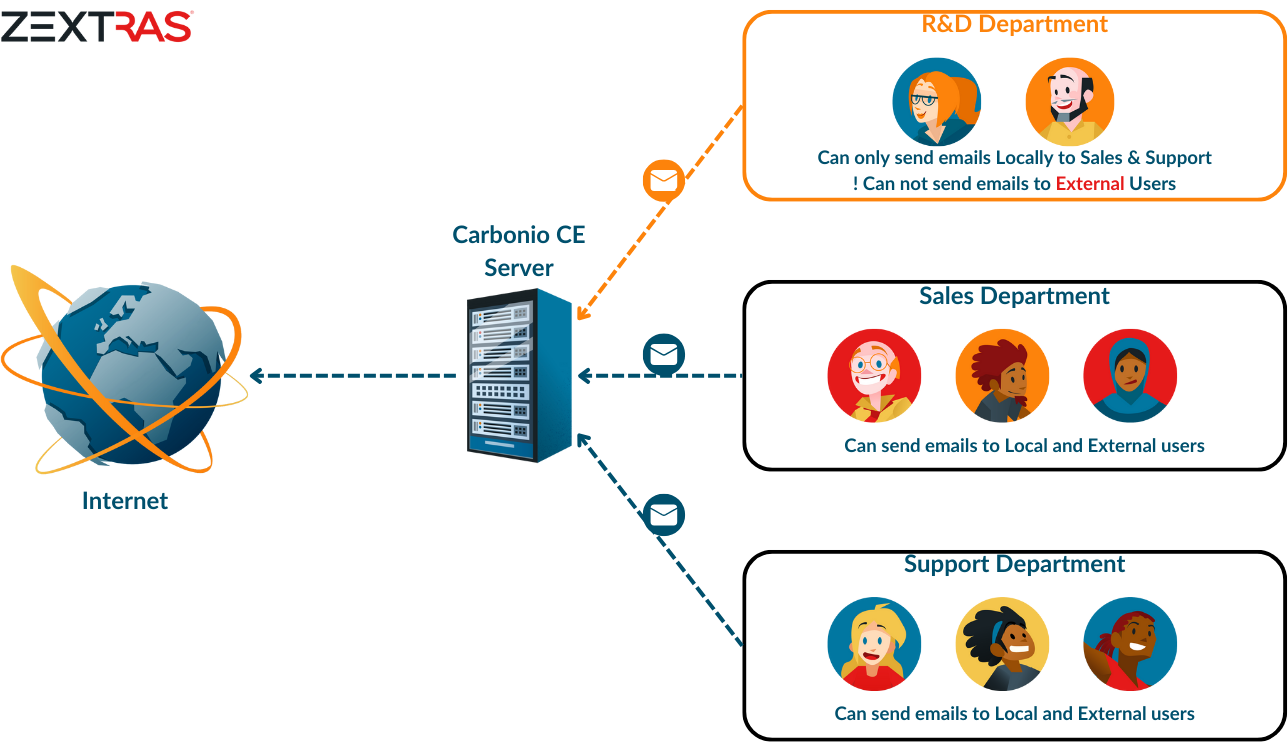
The consequences of a data breach in this scenario can be severe. Not only can it lead to financial losses for the company, but it can also damage its reputation and erode the trust of clients and stakeholders. How data breaching can cost and hurt an organization in today’s scenario, you can take a look at this article.
In this article, we will show how you can restrict/allow your users to send emails to both local and external users.
Add Restrictions To The MTA
Add the following line on top of /opt/zextras/conf/zmconfigd/smtpd_sender_restrictions.cf
%%contains VAR:zimbraMtaSmtpdSenderRestrictions check_sender_access lmdb:/opt/zextras/common/conf/restricted_senders%%Look at the example:
zextras@mail:~$ cat /opt/zextras/conf/zmconfigd/smtpd_sender_restrictions.cf
%%contains VAR:zimbraMtaSmtpdSenderRestrictions check_sender_access lmdb:/opt/zextras/common/conf/restricted_senders%%
%%exact VAR:zimbraMtaSmtpdSenderRestrictions reject_authenticated_sender_login_mismatch%%
%%contains VAR:zimbraMtaSmtpdSenderRestrictions check_sender_access lmdb:/opt/zextras/conf/postfix_reject_sender%%
%%contains VAR:zimbraServiceEnabled cbpolicyd^ check_policy_service inet:localhost:%%zimbraCBPolicydBindPort%%%%
%%contains VAR:zimbraServiceEnabled amavis^ check_sender_access regexp:/opt/zextras/common/conf/tag_as_originating.re%%
permit_mynetworks, reject_sender_login_mismatch
permit_sasl_authenticated
permit_tls_clientcerts
%%contains VAR:zimbraServiceEnabled amavis^ check_sender_access regexp:/opt/zextras/common/conf/tag_as_foreign.re%%
zextras@mail:~$Now modify the server using MtaSmtpdSenderRestrictions attribute:
zextras@mail:~$ carbonio prov ms mail.zextras.xyz +zimbraMtaSmtpdSenderRestrictions "check_sender_access lmdb:/opt/zextras/common/conf/restricted_senders"
zextras@mail:~$
zextras@mail:~$ carbonio prov gs mail.zextras.xyz zimbraMtaSmtpdSenderRestrictions
# name mail.zextras.xyz
zimbraMtaSmtpdSenderRestrictions: check_sender_access lmdb:/opt/zextras/common/conf/restricted_senders
zextras@mail:~$Modify Configuration File
Edit /opt/zextras/conf/zmconfigd.cf and find the section SECTION mta DEPENDS amavis (Line: 65). Add following lines before RESTART mta
POSTCONF smtpd_restriction_classes local_only
POSTCONF local_only FILE postfix_check_recipient_access.cfIt will look like:
root@mail:~# sed -n '280,286p' /opt/zextras/conf/zmconfigd.cf
POSTCONF smtpd_tls_session_cache_timeout LOCAL postfix_smtpd_tls_session_cache_timeout
POSTCONF smtpd_tls_session_cache_database LOCAL postfix_smtpd_tls_session_cache_database
POSTCONF smtpd_restriction_classes local_only
POSTCONF local_only FILE postfix_check_recipient_access.cf
RESTART mta
SECTION opendkim DEPENDS mta
zextras@mail:~$Now create the following file (/opt/zextras/conf/postfix_check_recipient_access.cf) and add mentioned line:
root@mail:~# cat /opt/zextras/conf/postfix_check_recipient_access.cf
check_recipient_access lmdb:/opt/zextras/common/conf/local_domains, reject
root@mail:~#Create a file for the users on whom we want to impose the restriction:
root@mail:~# cat /opt/zextras/common/conf/restricted_senders
researcher1@zextras.xyz local_only
root@mail:~#Now, create another file for the list of domains where the restricted users are allowed to send emails.
root@mail:~# cat /opt/zextras/common/conf/local_domains
zextras.xyz OK
root@mail:~#Remarks: If we leave this file empty then the restricted user will not be able to send email to anyone, even to himself. Also, we can add more email address or domains in this file.
Fix Permissions And Restart Services
Fix the permissions of following files:
root@mail:~# chown zextras:zextras /opt/zextras/conf/postfix_check_recipient_access.cf
root@mail:~# chmod 644 /opt/zextras/conf/postfix_check_recipient_access.cf
root@mail:~# chown :zextras /opt/zextras/common/conf/restricted_senders
root@mail:~# chmod 775 /opt/zextras/common/conf/restricted_senders
root@mail:~# chown :zextras /opt/zextras/common/conf/local_domains
root@mail:~# chmod 775 /opt/zextras/common/conf/local_domainsNow, postmap created files and restart the MTA service.
zextras@mail:~$ postmap /opt/zextras/common/conf/restricted_senders
zextras@mail:~$ postmap /opt/zextras/common/conf/local_domains
zextras@mail:~$ zmmtactl restartSo let’s see what we have achieved.
Right now, researcher1@zextras.xyz user is in the restriction list and it can only send emails to domain (zextras.xyz).
When Email Sent To zextras.xyz Domain
zextras@mail:~$ grep sales2 /var/log/carbonio.log | tail -n 1
Jul 4 18:08:07 mail postfix/lmtp[125232]: AE63028391B: to=<sales2@zextras.xyz>, relay=mail.zextras.xyz[185.213.27.93]:7025, delay=0.36, delays=0.01/0.02/0.05/0.29, dsn=2.1.5, status=sent (250 2.1.5 Delivery OK)
zextras@mail:~$When Email Sent To External Domain (Gmail)
zextras@mail:~$ grep imsilsa /var/log/carbonio.log | tail -n 1
Jul 4 18:07:34 mail postfix/smtpd[124536]: NOQUEUE: reject: RCPT from localhost[127.0.0.1]: 554 5.7.1 <researcher1@zextras.xyz>: Sender address rejected: Access denied; from=<researcher1@zextras.xyz> to=<imsilsa26112@gmail.com> proto=ESMTP helo=<mail.zextras.xyz>
zextras@mail:~$So this is how you can enforce restrictions and delivery policy for your users to control the data flow of your organization. Besides this kind of restriction, if you want to know how you can secure your users by blocking unwanted addresses, check out How to Blacklist/Whitelist address in Carbonio Community Edition Server.
In summary, restricting email users to local delivery is essential for enhancing security and protecting sensitive information. Implementing these email policies helps prevent unauthorized access and data leaks, ensuring a secure communication environment. Adopting these measures will safeguard your company’s data and build trust among stakeholders.
