Backscatter emails, a form of email abuse, can pose a serious threat to the stability and performance of your Carbonio Community Edition (CE) mail server. These unwanted messages, often generated by spammers forging the “From” address, can lead to excessive server load, reduced responsiveness for users, and even potential server crashes in extreme cases. Backscatter emails are also known as bounce-back spam, Non-Delivery Report (NDR) or a Non-Delivery Notification (NDN).
Let’s look at the scenario to understand how backscatter email attack works:
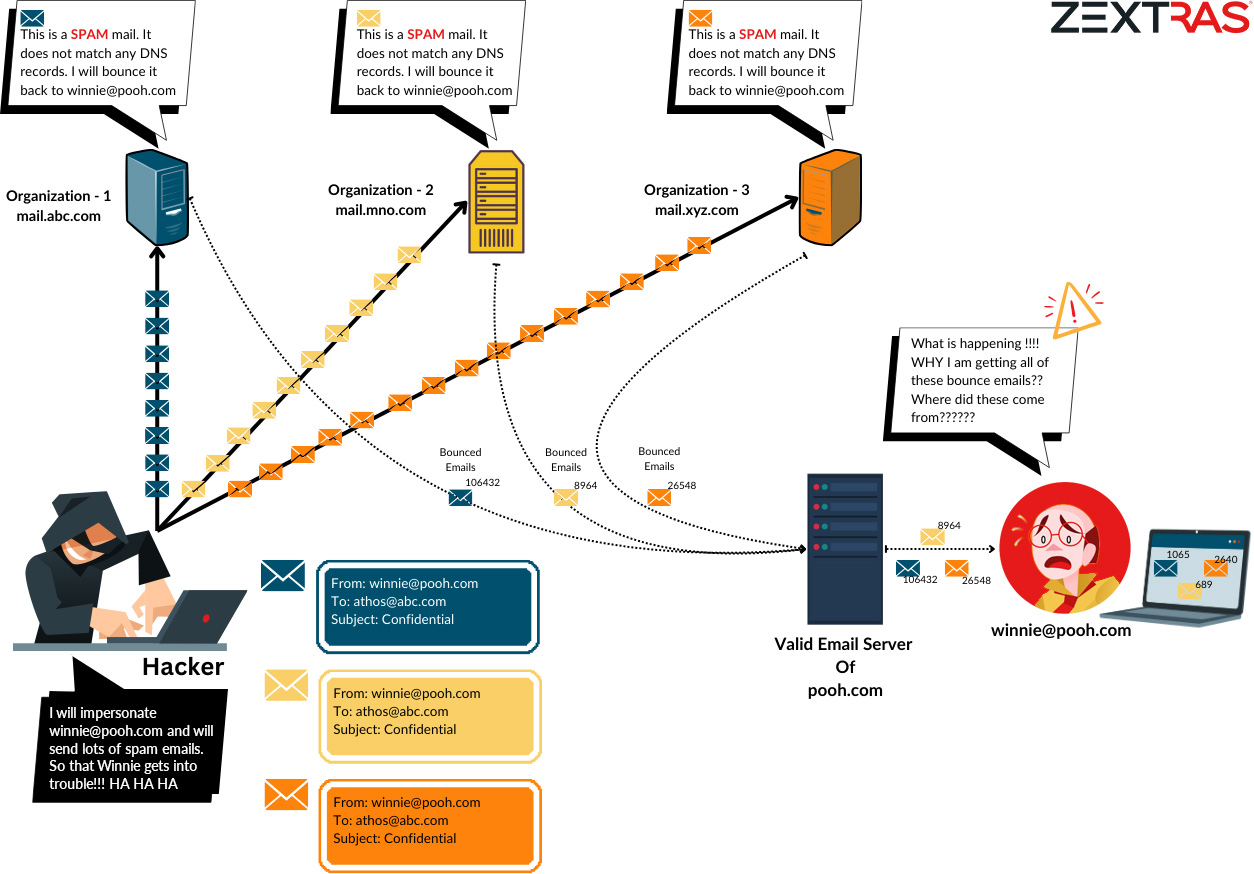
Impacts of Backscatter Emails
The impacts of backscatter emails can be significant and includes:
- Receiving a large volume of bounce-back messages resulting in cluttering user mailboxes
- Damages the reputation of the receivers’ address
- Overloading the email server with processing of a large volume of bounce messages resulting slow performance or outages
- High chance of getting Blacklisted by email service providers
- Email delivery rates for legitimate messages may decrease.
- Bounce-back messages can sometimes contain malware or links to phishing sites, posing security risks
- Recipients who receive what appear to be spam emails from a forged address may lose trust in the legitimate owner of that email address, impacting business relationships
If you want to know more about backscattering emails, read this article.
Prevention Steps for Backscatter Emails
By implementing these measures, you can significantly reduce the risk and impact of backscatter emails on your email infrastructure:
- Strengthen your SPF record to prevent email spoofing
- Deploy DKIM in your server to verify authenticity
- Properly setup DMARC for handling emails that fail SPF or DKIM checks, further securing email domains
- Configure mail servers to reject invalid emails during the initial SMTP connection stage
How to Get Rid of Backscatter Email Attack
- Login to your Carbonio CE server.
- Check the status of
zimbraMtaEnableSmtpdPolicydattribute.
root@mail:~# su - zextras
zextras@mail:~$ carbonio prov gcf zimbraMtaEnableSmtpdPolicyd
zimbraMtaEnableSmtpdPolicyd: FALSE
zextras@mail:~$ carbonio prov mcf zimbraMtaEnableSmtpdPolicyd TRUE- Enable
zimbraMtaSmtpdRejectUnlistedRecipientandzimbraMtaSmtpdRejectUnlistedSender
zextras@mail:~$ carbonio prov mcf zimbraMtaSmtpdRejectUnlistedRecipient yes
zextras@mail:~$ carbonio prov mcf zimbraMtaSmtpdRejectUnlistedSender yes- Check and set
zimbraMtaRestrictionAttribute:
zextras@mail:~$ carbonio prov gcf zimbraMtaRestriction
zimbraMtaRestriction: reject_invalid_helo_hostname
zimbraMtaRestriction: reject_non_fqdn_sender
zimbraMtaRestriction: reject_unknown_sender_domain
zextras@mail:~$
zextras@mail:~$ carbonio prov mcf +zimbraMtaRestriction “check_policy_service unix:private/policy”
zextras@mail:~$ carbonio prov gcf zimbraMtaRestriction
zimbraMtaRestriction: reject_invalid_helo_hostname
zimbraMtaRestriction: reject_non_fqdn_sender
zimbraMtaRestriction: reject_unknown_sender_domain
zimbraMtaRestriction: check_policy_service unix:private/policy
zextras@mail:~$
- Now restart services.
zextras@mail:~$ zmcontrol restartIf you are interested to strengthen your server security by blacklist/whitelist spammers or restricting users from exposing to external threats, check out our blog.
Protecting your Carbonio CE server from backscatter attacks is crucial for maintaining the integrity and reliability of your email communications. Implementing robust email authentication protocols such as SPF, DKIM, and DMARC can significantly reduce the risk of email spoofing, which is the primary cause of backscatter. Stay vigilant, regularly update your security configurations, and promptly monitor your email traffic to detect and mitigate any signs of backscatter.

Comments
This step did not work: $ carbonio prov mcf +zimbraMtaRestriction “check_policy_service unix:private/policy” I got this message: usage: modifyConfig(mcf) attr1 value1 [attr2 value2...] For general help, type : zmprov --help