It is becoming more and more important to ensure that organizations have the right to control their own data. Digital sovereignty is a concept that recognizes the power of organizations to protect their own data and use it to gain autonomy in their digital workplace. By putting the control in the hands of the individuals, digital sovereignty can help to protect data privacy, promote digital literacy, and ensure that individuals can make informed and empowered decisions about their online activities.
This article investigates the 6 pillars of digital sovereignty and their implications for individuals and organizations. By exploring how these levels of digital sovereignty interact with one another, we can gain a better understanding of how to protect our data and privacy online. Furthermore, we can use this knowledge to create more secure digital environments and ensure that our digital assets are protected.
What Is Digital Sovereignty?
Digital sovereignty is the right of an organization to maintain control over its digital data and infrastructure, ensuring that it remains secure and private. It is considered to be far vaster than data sovereignty, encompassing not only data, but also the infrastructure and its associated processes, services, and technologies.
The concept of digital sovereignty has become increasingly critical in the age of digital transformation, as organizations strive for autonomy and control over their data in a highly interconnected world.
How Organizations Can Achieve Data Sovereignty?
The first step an organization can take toward digital sovereignty is to create a comprehensive data governance policy. This policy should outline the organization’s approach to data security and privacy, as well as the roles and responsibilities of each stakeholder in the data governance process. The policy should also provide guidance on the types of data the organization will collect, store, and share, as well as the legal and ethical considerations associated with the data. The next step is to implement the data governance policy. This involves developing and deploying security measures, authentication, and access control, as well as developing processes and procedures for data storage and sharing. Additionally, organizations should consider using data analytics to identify and monitor potential risks and vulnerabilities.
In order for organizations to effectively implement their data governance policies, they need to have a comprehensive understanding of the different pillars of data sovereignty. This will make it much easier to effectively manage and protect their data.
Here are 6 pillars of digital sovereignty to help organizations understand the various dimensions of their digital presence and operations.
Understanding the different pillars helps us build proper data governance policies which eventually lead us to achieve digital sovereignty.
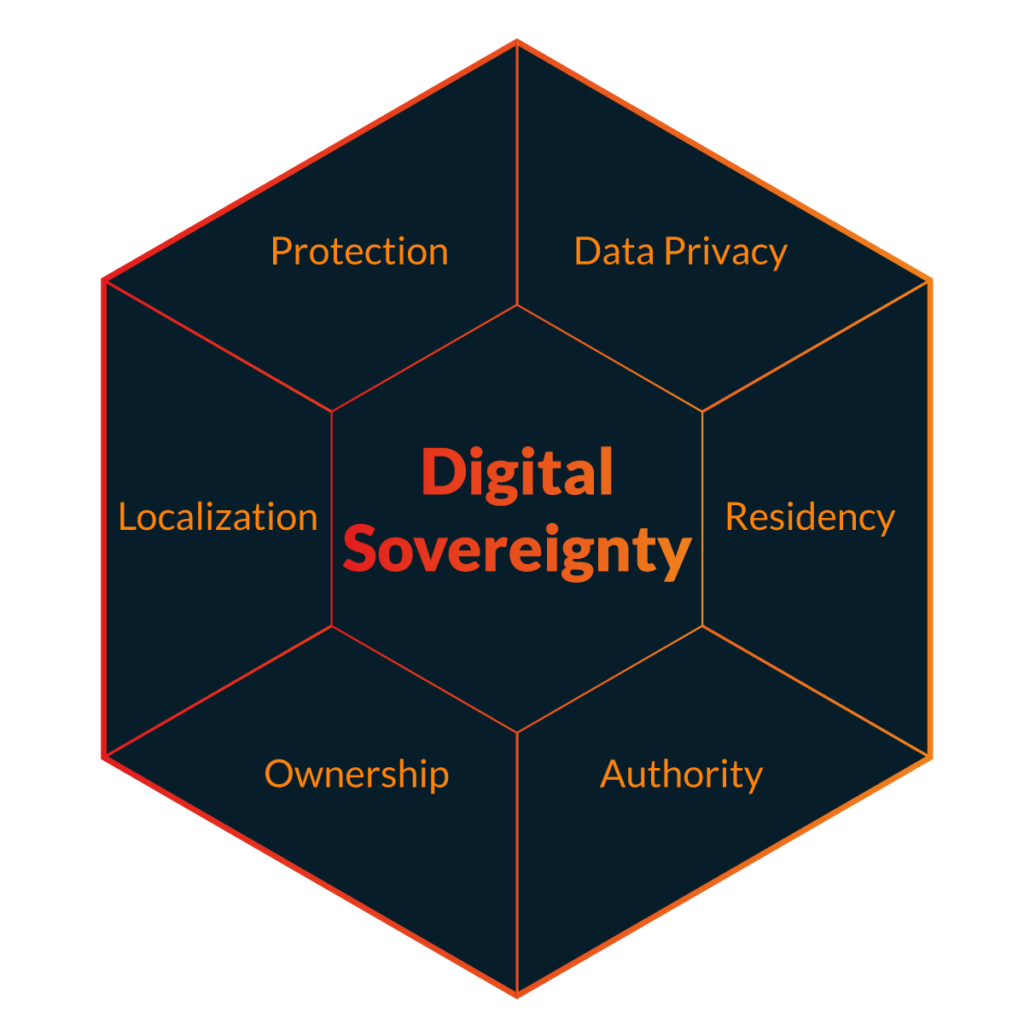
The privacy pillar is concerned with data and those who wish to keep control over it. This contains a sub-pillar of protection that ensures data is secure and access is allowed only when needed. The residency pillar deals with data that must follow mobility regulations and stay within a specific geographic area. The locality pillar necessitates that technology remains within the same confines, with nothing outside of them. The authority pillar governs who has access to services, infrastructure, and assets. Finally, the ownership pillar defines the legal ownership restrictions for those same services, infrastructure, and assets.
Pillar 1 – Protection
This implies that the data, software, and infrastructure in a company are securely protected by a variety of measures, such as firewalls, secure authentication, and backup systems. These measures are designed to ensure that confidential information is not accessed or altered without authorization. Additionally, regular security audits, user access monitoring, and regular updates to security protocols are all employed to ensure the highest level of protection. It’s the first step towards achieving digital sovereignty, yet it is often overlooked by many organizations.
Pillar 2 – Data Privacy
External access to personal and sensitive data can be a serious problem, not just for hackers, but also for improper use or foreign governments. That is why data protection regulations like the GDPR have strict requirements for the protection of personal data. These requirements ensure that individuals’ data is kept secure and handled responsibly.
One of the best ways to protect data against these threats is to keep it in the hands of the people who own it. By securely storing personal data in the possession of its rightful owners, the risk of it being stolen or accessed by unauthorized individuals is significantly reduced. This can be achieved by utilizing data centers located on the organization’s premises, taking advantage of the latest technologies and infrastructures for maximum privacy and security. Another option would be to leverage the benefits of private clouds, which offer greater flexibility, control over data security and privacy, and increased reliability compared to public cloud computing.
Pillar 3 – Residency
Data residency is the requirement that data must remain within the confines of a country’s physical boundaries, ensuring that it is not transferred, processed, or stored in any other country. Data residency is also a legal term that refers to the physical location where data is stored. In order for a company to be considered a data resident in a specific country, it must meet certain requirements, including having its servers and personnel located in that country. This can be important for companies that want to avoid potential tax liabilities or regulations related to data processing.
Proponents of data residency argue that it is important for data to be located within a specific jurisdiction in order to ensure that data is protected from unauthorized access and abuse. They also argue that it is easier to control data if it is located within a specific jurisdiction.
Pillar 4 – Locality
Locality refers to the geographical and physical location of data and the associated infrastructure necessary to support data processing. This infrastructure may include networks, storage, servers, and other hardware and software components that must reside within the country’s boundaries.
This concept may be somewhat challenging to understand, so let’s clarify it with the help of an example. For instance, let’s consider the most famous hyper-scale public cloud providers; data may be stored in a data center inside the country, while other components that run and process data may be hosted in the cloud or on remote servers in another country. Locality, however, refers to the geographical proximity of data and its associated infrastructure. This can be achieved using self-hosted servers on the premises of the organizations.
Pillar 5 – Authority
Authority in digital sovereignty terms means you have control over who has access to which information, allowing you to protect sensitive information and ensure that only authorized individuals are welcome.
Information can be controlled by individuals or organizations by using different methods. At an individual level, you can control information by keeping it confidential while controlling information access at an organizational level is more complex. The application should give you the ability to control information by restricting who can access it.
Pillar 6 – Ownership
Ownership is a concept related to the entire environment where data, applications, and workloads are managed and controlled by an entity. It is essential to ensure that the owner has the necessary authority to manage and protect these resources and outlines the legal boundaries of ownership of services, infrastructure, and assets.
Similar to the locality, this can be also made possible thanks to self-hosted servers on the premises of the organization, providing the utmost reliability, security, and accessibility to data and applications.
Why Do Organizations Care about Digital Sovereignty?
The need for digital sovereignty expands beyond the organizations’ internal requirements. In the past years, governments have constantly increased the sovereignty measures expected from organizations and this trend does not seem to be stopping. The recent changes in geopolitical affairs, especially in Europe, have given rise to this question: when using cloud services, if the relationship with the service provider and/or its government changes, will it be possible to keep using our systems in a sustainable, secure, and affordable manner?
Achieving digital sovereignty is already the main subject of digital transformation in many companies, especially in the EU with the emergence of the General Data Protection Regulation (GDPR). As per a recent report in The New York Times, more than 50 nations are attempting to regulate the digital information generated by their citizens, governments, and businesses. Factors such as security, privacy issues, economic considerations, and even territorial conflicts have led governments to do their utmost to erect a wall around the data within their boundaries and set standards for where it can and can’t be sent.
