An email server contains several layers of security. As a system admin you may be familiar with all of them but we can not expect this expertise from a regular user. Though there is one aspect of security that involves both system admins and the users. That is the password policy. In this article, we are going to discuss this in details.
Purpose Of This Article
The purpose of this article is to make system admins aware of current standard guideline of setting an effective password policy. Also, system admins should understand the importance of these guidelines so that they can convince a regular/non tech user to understand and get used to these guidelines and comply with them. Finally, we will see how you can set an effective password policy as a system administrator and as a user what type of password you should use.
This is a common issue that almost every system admins face. A conflict between users and system admins. But it can be resolved if we can get both of them on the same page regarding a good password policy and it’s enforcement. 😊
Standard Guidelines For Password Policy
There are lots of insightful guidelines available on the internet. To save your time, let me summarize some key points that you can follow as a guide line:
- Use a minimum length of 14-character password.
- Make mandatory use both Upper & Lower case letters in a password.
- Make mandatory use of numeric characters in a password. (0-9)
- Make mandatory use of special characters in a password. (e.g. ~!@#$%^&*()_-+=)
- Do not use word or series of words from any dictionary.
- Do not use personal information (i.e. user ID, name, pet, designation etc.) in the password.
- Do not use sequential characters (i.e. 1234) or repeated characters (i.e. aaaa)
- Change the password at the first login.
- Use blank spaces in the password/passphrase.
- Do not use same password in multiple sites or accounts.
- Do not reuse password if possible.
- Use passphrase instead of password using above mentioned parameters. Check out this link to know more about passphrase. You can also check out this link to generate some cool passphrase.
If you have interest to read more on this topic, you can visit this page:
NIST Password Guidelines
A system admin should set the password setup policy as per above mentioned guideline. But most importantly, they should convince and train their end users to follow these guidelines during setting up password for their respective account.
Importance Of The Guideline
We just described some major guidelines for an effective password policy. But how can we get both system admin and end users on the same page?
If only both system admins and end users realize the importance of following these guidelines. So what are the possible importance of these guidelines?
Let’s take a look.
- Any password that is created by following the guideline is harder to crack.
- Any password that is created by following the guideline is also harder to remember, it prevents the end user reuse old passwords.
There are sites like this one: Breached Password Database where you can check whether your password is breached or not.
You can also find lot’s of useful contents on the internet to understand the importance of a strong password policy guideline.
So in-spite of end users reluctance, it is mostly a system admins responsibility to convince the user to comply with the policy.
Password Policy In Carbonio CE Admin Panel
By Default, all email accounts on Carbonio CE inherits the password policy (like all other policies) from the Class Of Service (COS) feature.
So you can make necessary policies in the COS and all accounts will be forced to comply with it.
To get to the password policy on the Carbonio CE admin panel, you need to login into the admin panel using admin user. Then go to:
Home > COS (Select the COS) > Advanced (Password)
Now let’s see what do we have in Advanced (Password) section:
- Prevent user from changing password – As a system admin, if you need you can prevent users from changing the password.
- Minimum password length – Default value of this field is 6. So users can not set any password that has less than 6 characters. But we would recommend the the minimum password length should be at least 12.
- Maximum password length – Default value of this field is 64. So users can set a password that has total number of characters up-to 64.
- Minimum upper case character – Default value of this field is 0. That means users do not need to use any upper case character while constructing any password. But check out our guidelines! It is strongly recommended to use at least one upper case character in your password.
- Minimum lower case character – Default value of this field is 0. That means users do not need to use any lower case character while constructing any password. But check out our guidelines! It is strongly recommended to use at least one lower case character in your password.
- Minimum punctuation symbols – Default value of this field is 0. But set a policy in a way that users are forced to use at least one punctuation symbol in the password.
- Minimum numeric characters – Default value of this field is 0. But it is recommended that users password should at least 1 numeric character.
- Minimum password age (Days) – The Minimum password age policy setting determines the period of time (in days) that a password must be used before the user can change it. You can set a value between 1 and 998 days, or you can allow password changes immediately by setting the number of days to 0.
- Minimum password age (Days) – Default value of this field is 0. Set Maximum password age to a value between 30 and 90 days, depending on your environment. This way, an attacker has a limited amount of time in which to compromise a user’s password and have access to your network resources
- Minimum numeric character or punctuation symbols – In-spite of setting individual parameters fro punctuation or numeric value, you can use this field to specify how many numeric or punctuation a password should contain.
- Minimum number of unique password history – The Minimum number of unique password history policy setting determines the number of unique new passwords that must be associated with a user account before an old password can be reused. Therefore, is this field has a value of 6 then until the user uses 6 unique passwords, they can not reuse old passwords.
- Reject common passwords – By enabling this option, you can prevent users from setting common passwords.
Let’s take a look at the interface:
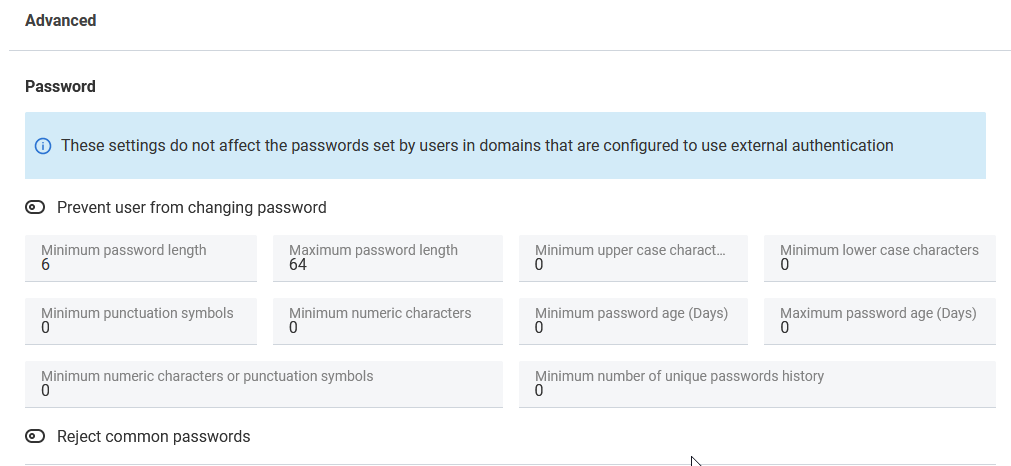
So now, as a system admin what should be your approach to set a default password policy for all of your users.
How A User Should Set The Password
As I have mentioned earlier that it is mostly system admins responsibility to convince and train users to follow the password policy guideline (If users are privileged to set their own passwords). But non tech users may face difficulty to match all parameters we mentioned earlier.
Therefore, as a tech genius you can help them with several online tools (Which can help them to create a password compliant with all conditions) and can become a Hero in the office. 🤩
- There are few useful password generator sites that can help users to generate strong password without breaking a sweat.
- Users can also use passphrase generator.
- Users can use password manager which can help them to not only generate passwords/passphrases but also helps them to save these keys in a secure way (Which is another important thing besides generating/constructing a password/passphrase)
So this is it.
It is a long article. But I hope it will help you to understand how important it is to set a good password policy and more importantly getting all the end on the same page with you to follow the policy.
Let’s do this.
😊
