Carbonio Proxy is one of the required Carbonio CE mail server nodes. It is a combination of Nginx and Memcached servers, which perform several functions at once, ensuring the high efficiency and security of using Carbonio CE. In this article, we will talk about exactly what functions Carbonio Proxy performs and how an administrator can interact with it.
Functions and Structure of Carbonio Proxy
As already mentioned, the Carbonio Proxy node is a combination of Nginx and Memcached servers. They perform several functions at once, allowing you to increase the security of using Carbonio, and at the same time increase its speed.
Centralized Email Access
The main function of Carbonio Proxy is to provide users with access to their mailboxes. Carbonio Proxy redirects request from users to servers that store their email, address books and calendars. This is of the greatest value in multi-server systems, as it allows users not to remember the exact name of their mail server and use a single login address.
Carbonio Proxy processes request via HTTPS/POP/POPS/IMAP/IMAPS protocols, redirecting them to the appropriate mail servers. SMTP requests, in turn, are not proxied and are sent directly to the MTA server. Carbonio Proxy requires that it be accessible on TCP ports 80, 443, 110, 995, 143, 993, and 6071 for incoming connections, and TCP ports 7072, 8080, 8443, 7110, 7995, 7143, 7993, and 7071 for outgoing connections.

Load Balancing
This feature is extremely useful in multi-server systems. It allows you to distribute users between mail storages in such a way that the load on them is even and there are no situations in which one server cannot cope with the number of incoming requests, while others are idle.
Reverse Proxy
Using a centralized mail server login allows you to hide the topology, names, and characteristics of various hosts by placing them on a non-public internal network. This makes system nodes inaccessible to denial of service (DoS) attacks and malware.
SSL Termination
Encrypting a connection in highly loaded systems can consume most of the computing power. In order to direct this power to ensure system performance and perform basic functions, SSL termination is used, which occurs on the Carbonio Proxy node. After the data is decrypted, it is transmitted to other nodes in a non-public local network in an unencrypted form.
Note that the use of this function is potentially unsafe and should only be used in cases where you are completely sure of the security and isolation of your local network.
By the way, in one of the recent Carbonio CE updates, the ability to use Carbonio Proxy in HTTP mode was removed. Now only two modes of operation are available to the administrator:
- HTTPS – when accessing HTTP the user gets an error
- Redirect – when accessing via HTTP, the user is redirected to the same address, but via HTTPS
Thus, the use of SSL encryption is mandatory for Carbonio at this time. You can change the mode of operation using commands carbonio prov modifyServer proxy.carbonio.loc zimbraReverseProxyMailMode redirect and carbonio prov modifyServer proxy.carbonio.loc zimbraReverseProxyMailMode https

Caching
The built-in Memcached server allows Carbonio Proxy to remember user routes to mail stores and instead of performing searches, use existing routes to increase system performance and overall responsiveness.
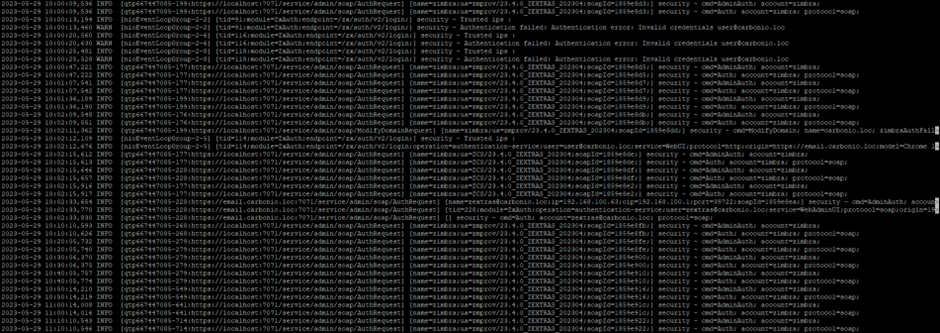
Access Logging
On Carbonio Proxy nodes, the /opt/zextras/log/audit.log file stores information about successful and unsuccessful user login attempts. Thanks to monitoring logs, you can track an attempt to hack an account in time and take the necessary measures to counter it.
Also, Carbonio Proxy nodes are often used to display web client and admin console interfaces, while the back end of these applications resides on mail servers.
SNI and Virtual Hosts
Since Carbonio is a multi-tenant solution that allows you to create many mail domains on the same infrastructure, one of the important features is SNI – Server Name Indication. This technology allows you to create publicly available virtual hosts in Carbonio Proxy with their own SSL certificates, available at the same IP address.
You can create virtual hosts both on the command line and in the admin panel.
In the admin panel, go to the “Domains” section and enter the name of the domain for which you are going to create a virtual host. In the side menu that opens, select the section “Virtual hosts & certificates”
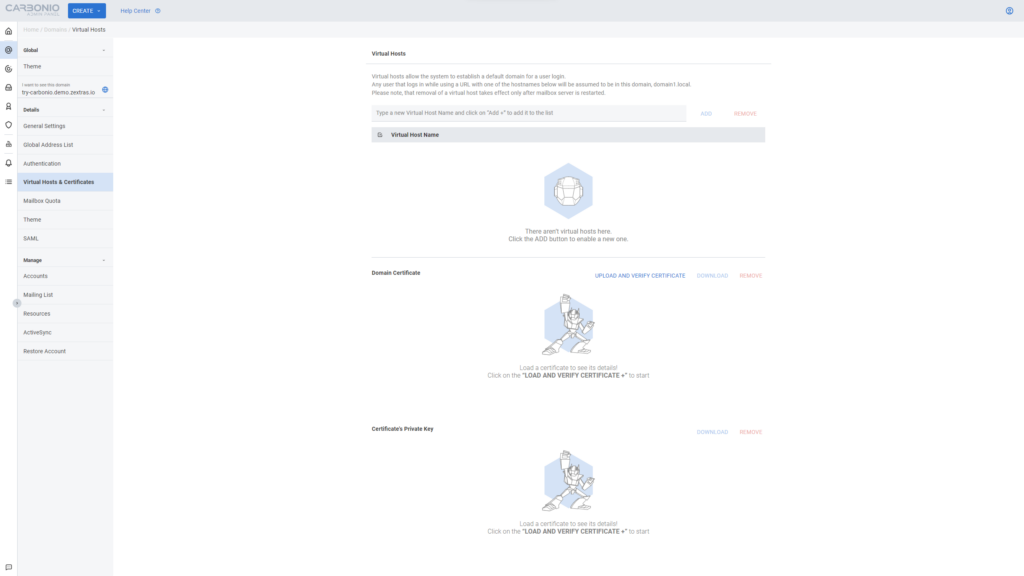
In the window that opens, you can add virtual host names for the domain, as well as install SSL certificates for them. Multiple virtual hosts can be added for each of the domains, the only requirement is that they must be valid, DNS-resolvable FQDNs.
On the command line, a virtual host can be added with a command like carbonio prov modifyDomain carbonio.loc zimbraVirtualHostName carbonio.tld. To add additional virtual hosts, use the command carbonio prov modifyDomain carbonio.loc +zimbraVirtualHostName mail.carbonio.tld.
Note that virtual hosts only work for the HTTPS protocol. In order for them to work, including for POP / POPS and IMAP / IMAPS, you need to add a virtual IP address. It is added with a command like carbonio prov modifyDomain carbonio.loc zimbraVirtualIPAddress 1.2.3.4.
Multiplicating Carbonio Proxy
As with any node in Carbonio CE, a multi-server installation allows the addition of two or more servers with the Proxy role. To install an additional Carbonio Proxy node, on a machine with a configured Carbonio repository, install the packages apt install service-discover-agent carbonio-proxy carbonio-webui carbonio-files-ui carbonio-chats-ui
After the installation is complete, run the carbonio-bootstrap command, and during node setup, specify the LDAP server address and password and register the node with Carbonio Mesh using the service-discover setup-wizard and pending setups commands. After that, an additional Carbonio Proxy node will appear on your system.
However, given that Carbonio Proxy itself is the entry point to the mail system and acts as a load balancer for other nodes, the question arises of how exactly the load should be balanced between the Carbonio Proxy nodes themselves. For this, an external load balancer is used. As a rule, a HAProxy server with a public IP address is used for this purpose.
