One fine summer afternoon, you found that one of your users account has become compromised and it has been generating huge amount of SPAM mails. In this article, we will discuss possible reasons, aspects so that we can decide what to do in that scenario.
It will be a series of articles and this is the first one in this series.
So let’s start the discussion.
Let’s try to understand the situation
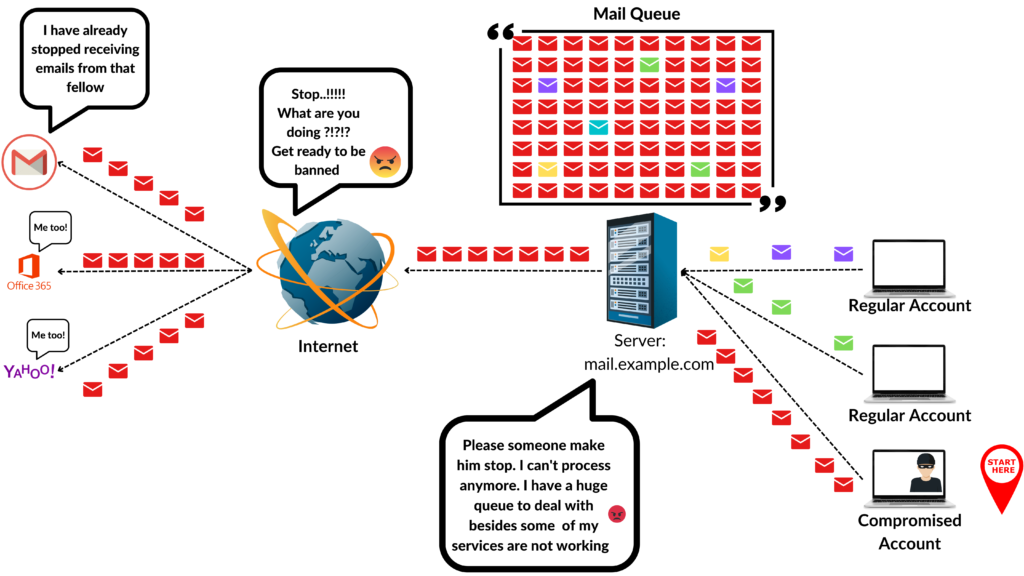
One of your users’ account got compromised. It is generating huge amount of random unsolicited SPAM mails. So within few minutes you will notice following things:
- You mail server will pass/forward thousands of unwanted emails to random destinations causing significant reputation damage to your IP address and domain.
- Due to very high amount of email, eventually your email server’s mail processing capacity will crash, resulting an interruption in mail transitions.
- As your server’s mail processing will stop working,
mail queuesize of your server will grow enormously and only adding to your trouble. - Due to this heavy load, it is possible that your server may show less response to your troubleshooting activity
What can cause this ?
A compromised email account is the main reason for this kind of incident. But what causes an email account to be compromised:
- May be user’s workstation is infected with malicious application/software.
- Most of the time users save their credentials in the web browser, which is very much exploitable by the external threats
- May be user’s email account credential has been compromised
- User may have clicked/opened malicious infected email with attachment.
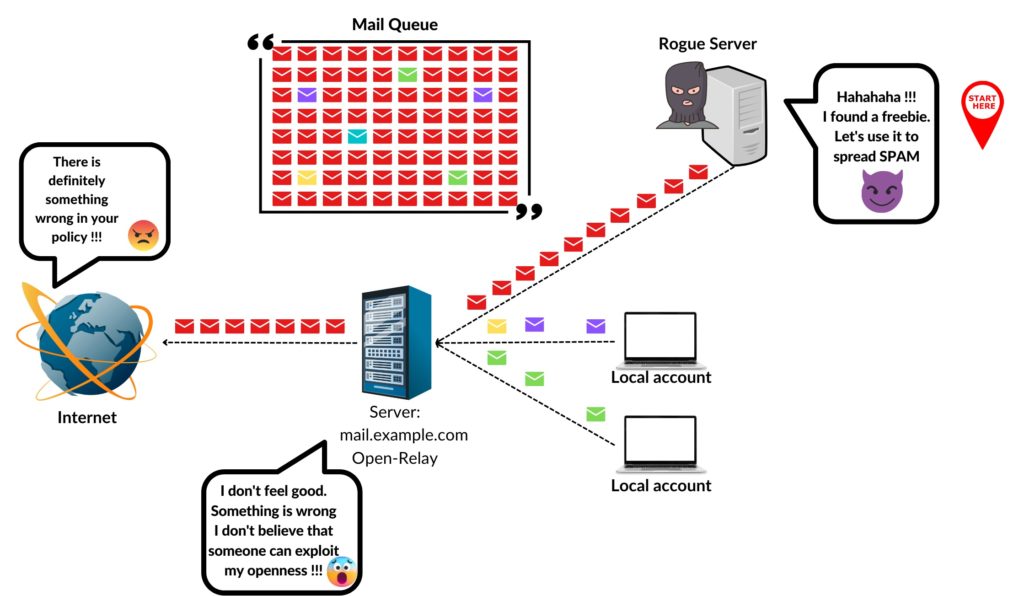
Besides these user specific reasons, there can be some other critical facts that can cause the spamming. Like,
- If your email server is an open relay then remote exploiters can use your server to relay their spam mails and it happens a lot.
It’s time for damage control
As soon as you find the the spamming incident, start your damage control immediately. If you are wondering how you can detect spamming before it does that much damage, check out our this article.
Check the current mail queue status:
root@mail:~# /opt/zextras/libexec/zmqstat
corrupt=0
hold=0
active=9058
deferred=5742
incoming=0
root@mail:~#As you can see lot’s of emails in deferred and active queue which is quiet unusual.
Now let’s find out from which account the emails are generating:
zextras@mail:~$ mailq|grep ^[A-F0-9]|cut -c 42-80|sort |uniq -c|sort -n|tail
1 flaminia@example.com
1 irene@example.com
1 paolo@example.com
1 stefania@example.com
1 zextras@example.com
2 arman@example.com
13 suman@example.com
5658 suman@example.com
9117 suman@example.com
zextras@mail:~$Now take a close look at the /var/log/carbonio.log to find out the originating IP and block it from connecting to your server.
Also, if needed change the compromised user’s email account credential. Make your server from open relay to closed authenticated relay server.
Now, put all mails of the queue on hold.
root@mail:~# /opt/zextras/common/sbin/postsuper -h ALL
postsuper: Placed on hold: 14805 messagesNow we need to clear these unwanted mails from the mail queue to make the whole system functional again. To do that, we will use postsuper to delete all hold mails from the mail queue.
root@mail:~# /opt/zextras/common/sbin/postsuper -d ALL hold
postsuper: Deleted: 14805 messages
Now as you have deleted all mails from the mail queue, re-queue all current emails so that your email transaction becomes normal again.
postfix flushWhat could have done to prevent this?
You can take many approaches to prevent spamming in your server. Let’s take a look at some of them:
- Keep your user accounts secure by using complex passwords. Make a habit of changing password at a regular interval.
- Make sure that your users workstation and application are safe and not affected by any malware.
- Don’t let your email server be an open relay. Only pass authenticated messages.
- Set mail sending rate limit in your server so that in case of violation of previous approaches, your server can block spam mail flood.
- If there is a firewall in your network, place your email server behind the firewall.
- Use email security appliances to protect your server from any mail borne threats.
- Enforce necessary policy at your server’s firewall, MTA to strengthen it’s robustness.
- Keep your server updated with latest software version and patches specially those are related to security.
So these are the basic facts that you should consider during an ongoing spamming incident. Your timely initiative can reduce the damage significantly. For that, you have to collectively use all of these approaches.
Hope this information is helpful to you.
That’s it for today.
😊
