A centralized authentication system is one of the easiest and most efficient methods for managing password security policies within an enterprise. Since authentication is handled by a single server, any password changes are also managed within one system, allowing for the password security policy to be set up just once. In this article, we will discuss how to integrate Carbonio CE with external Active Directory or LDAP systems commonly used for user authentication in enterprise environments.
Active Directory Authentication
External authentication with an existing Active Directory server can be configured either through the Admin Panel or via the command line.
When a user inputs their account name and password, the data isn’t matched with password hashes stored in Carbonio LDAP. Instead, it is sent to an external AD server for authentication. Following the verification, Carbonio receives a response from Active Directory, indicating either successful authentication or failure. Depending on this response, the user is either granted access or shown the appropriate error message.
To configure this in the admin panel, navigate to Domains > select your domain > Authentication.
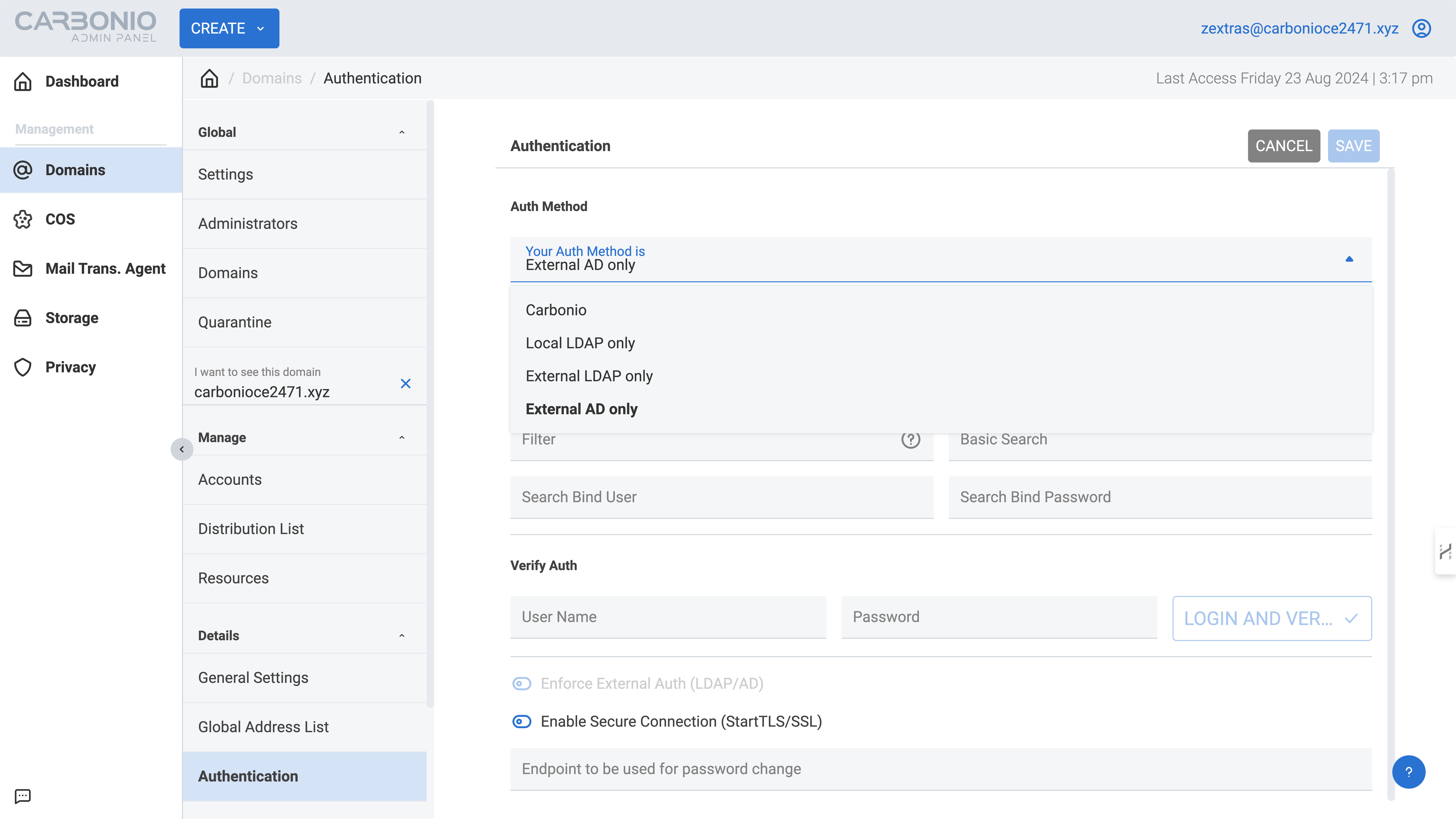
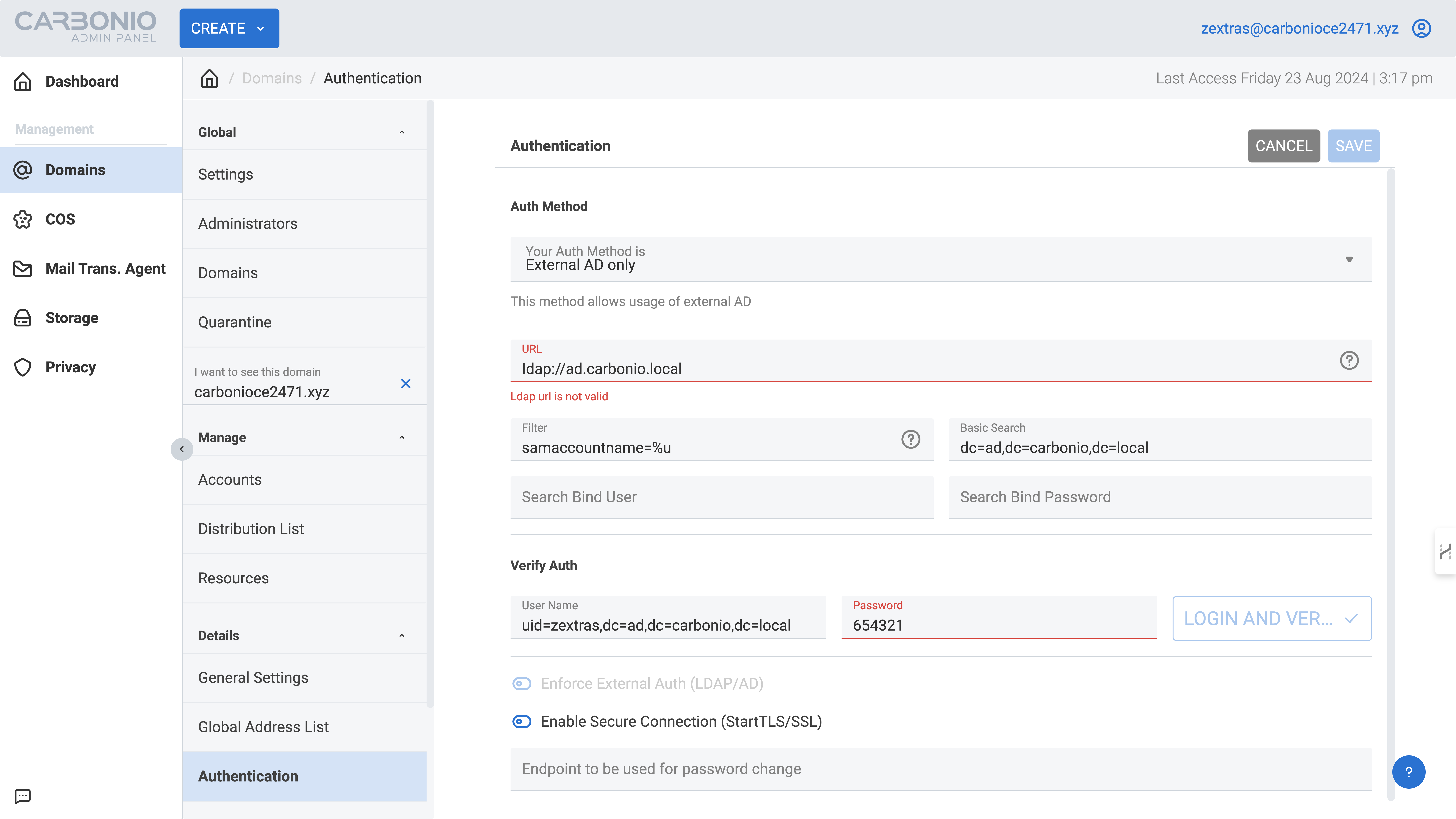
In the window that appears, choose the external Active Directory authentication method and enter the required parameters:
- Distinguished name template: Use macros such as
%u(e.g.,uid=%u,dc=ad,dc=carbonio,dc=local). - URL: Provide the domain name or IP address of the AD server (e.g.,
ad.carbonio.local:389). - Filter: Use a filter to restrict accounts to live users in the domain (e.g.,
samaccountname=%u). - Basic Search: Define a query to find all accounts within the domain (e.g.,
dc=ad,dc=carbonio,dc=local). - Username: Enter a username with read permissions on the LDAP branch where your mail domain accounts are stored (e.g., the AD global admin).
- Password: Specify the password for the user with read rights on the LDAP branch where your mail domain accounts are stored (e.g., the AD global admin password).
Below the option “Try local password management using other methods if this fails,” you can enable the use of your local Carbonio password in addition to the Active Directory password for login. This feature is helpful if the AD server becomes unavailable or encounters issues.
Once all settings are entered, click the “Login and Verify” button to verify the data. If the connection is successful, click “Save” to finalize and save the configuration.
For command-line configuration, several attributes need to be modified for the custom domain. Here’s an example using the mail domain test.carbonio.local, with users being authenticated in the ad.carbonio.local domain:
- Authentication mechanism:
carbonio prov modifyDomain test.carbonio.local zimbraAuthMech ad- Distinguished name template:
carbonio prov modifyDomain test.carbonio.local zimbraAuthLdapBindDn uid=%u,dc=ad,dc=carbonio,dc=local- Username for LDAP searches:
carbonio prov modifyDomain test.carbonio.local zimbraAuthLdapSearchBindDn uid=zextras,dc=ad,dc=carbonio,dc=local- Password for LDAP searches:l
carbonio prov modifyDomain test.carbonio.local zimbraAuthLdapSearchBindPassword 654321- Basic Search:
carbonio prov modifyDomain test.carbonio.local zimbraAuthLdapSearchBase dc=ad,dc=carbonio,dc=local- Search filter:
carbonio prov modifyDomain test.carbonio.local zimbraAuthLdapSearchFilter samaccountname=%u- Active Directory server URL:
carbonio prov modifyDomain test.carbonio.local zimbraAuthLdapURL ldap://ad.carbonio.localTo enable the use of local Carbonio passwords alongside AD passwords, use:
carbonio prov modifyDomain test.carbonio.local zimbraAuthFallbackToLocal TRUE
To disable this feature, use:
carbonio prov modifyDomain test.carbonio.local zimbraAuthFallbackToLocal FALSE
User authentication with external LDAP is configured similarly to the process for Active Directory.
User Authentication Outside the Template
The example above applies to the entire domain and works correctly only if the Active Directory or LDAP domain has user accounts with matching names in Carbonio. If user accounts in Active Directory or LDAP have different names, you’ll need to configure a unique BindDN for each user.
This can be done via the command line. For example:
carbonio prov modifyAccount zextras@test.carbonio.local zimbraAuthLdapBindDn uid=admin,dc=ad,dc=carbonio,dc=localThis command links the Carbonio account zextras@test.carbonio.local to the admin@ad.carbonio.local account.
If template authentication is already configured for the domain, accounts that match the template will authenticate using the existing settings, and no additional Bind DN configuration will be necessary for them.
