Strong and constantly changing passwords are the basis for protecting your accounts from hacking. This is why a strong password security policy is the first thing a Carbonio CE mail server administrator needs to set up to increase the level of security for accounts on the server. The second necessary action is to ensure strict compliance with password policy requirements by all users. In this article, we will talk about how to set up a password security policy in Carbonio CE and how to get users to comply with it.
The key points of a strong password policy are increased requirements for password strength and frequency of password replacement. Carbonio CE allows the administrator to not only configure these settings but also automate the monitoring of user compliance with them.
You can configure a password security policy both for individual users and for entire classes of service. The settings themselves can be changed in the graphical administrator console and in the command line.
In Carbonio’s Admin Panel, password security policy can be configured at the Class of Service – COS level. To do this, select the COS section in the right sidebar and select the Class of Service for which you will configure the password security policy.
Please note that the password policy settings you have applied will not take effect if you are using an external LDAP server or AD to authenticate users.
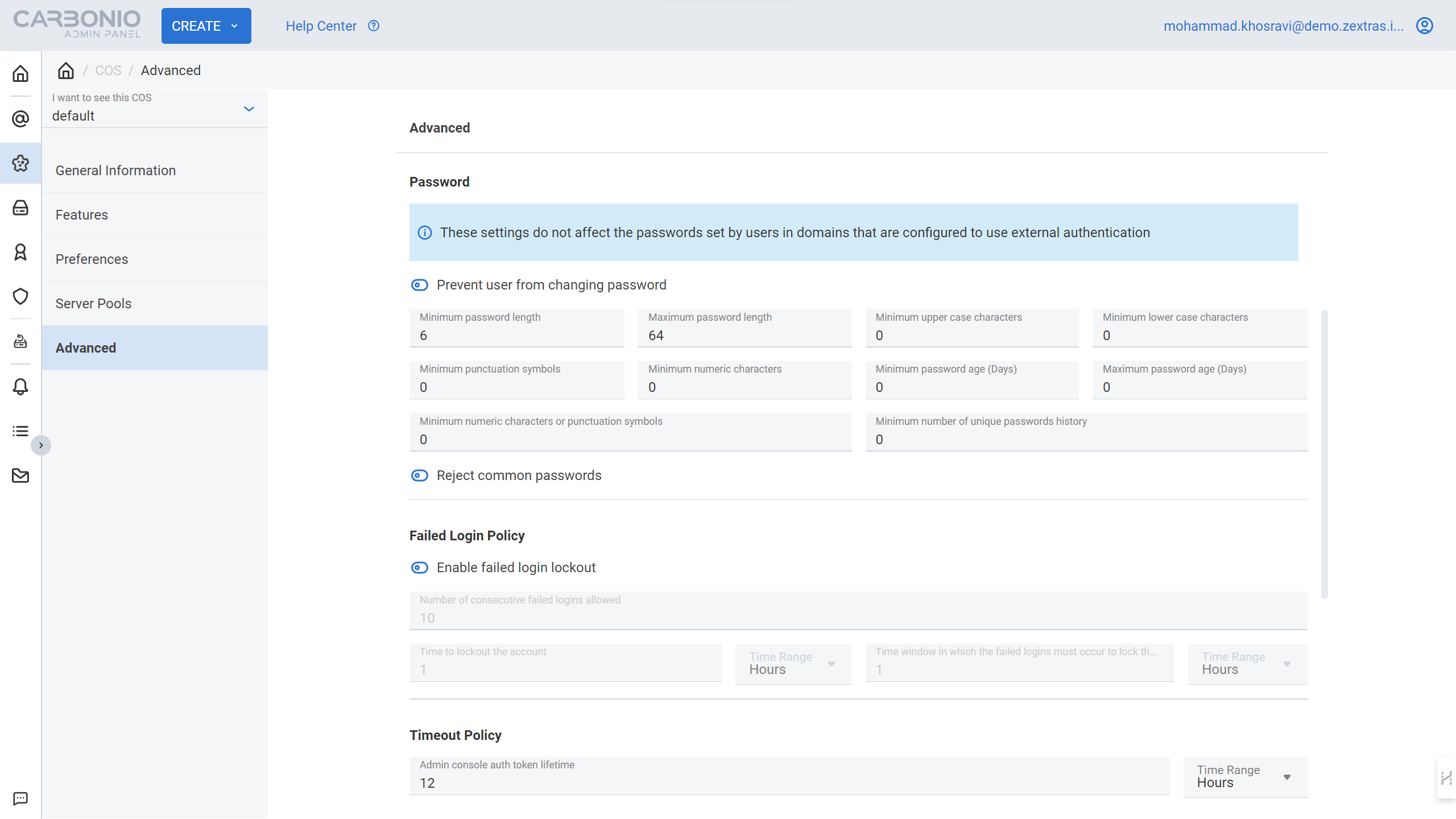
The following options are available for configuration:
- Prevent user from changing password
- Minimum number of unique passwords
- Maximum password lifetime (days)
- Maximum password length
- Minimum password lifetime (days)
- Minimum number of numbers or punctuation symbols.
- Minimum password length
- Minimum number of lowercase characters
- Minimum number of digits
- Minimum number of punctuation symbols
- Minimum number of uppercase characters
- Prohibition of dictionary passwords.
On the command line, password security policy settings can be changed at both the Class of Service and user levels.
To change at the user level, use the commands, replacing user@domain.tld with your user name:
carbonio prov modifyAccount user@domain.tld zimbraFeatureChangePasswordEnabled
carbonio prov modifyAccount user@domain.tld zimbraPasswordEnforceHistory
carbonio prov modifyAccount user@domain.tld zimbraPasswordMaxAge
carbonio prov modifyAccount user@domain.tld zimbraPasswordMaxLength
carbonio prov modifyAccount user@domain.tld zimbraPasswordMinAge
carbon prov modifyAccount user@domain.tld zimbraPasswordMinDigitsOrPuncs
carbonio prov modifyAccount user@domain.tld zimbraPasswordMinLength
carbonio prov modifyAccount user@domain.tld zimbraPasswordMinLowerCaseChars
carbonio prov modifyAccount user@domain.tld zimbraPasswordMinNumericChars
carbonio prov modifyAccount user@domain.tld zimbraPasswordMinPunctuationChars
carbonio prov modifyAccount user@domain.tld zimbraPasswordMinUpperCaseChars
carbonio prov modifyAccount user@domain.tld zimbraPasswordMinAlphaCharsBy default, the user is allowed to create any password between 6 and 64 characters.
To change at the Service Class level, use the commands, replacing default with the name of your Service Class:
carbonio prov modifyCOS default zimbraFeatureChangePasswordEnabled
carbonio prov modifyCOS default zimbraPasswordEnforceHistory
carbonio prov modifyCOS default zimbraPasswordMaxAge
carbonio prov modifyCOS default zimbraPasswordMaxLength
carbonio prov modifyCOS default zimbraPasswordMinAge
carbonio prov modifyCOS default zimbraPasswordMinDigitsOrPuncs
carbonio prov modifyCOS default zimbraPasswordMinLength
carbonio prov modifyCOS default zimbraPasswordMinLowerCaseChars
carbonio prov modifyCOS default zimbraPasswordMinNumericChars
carbonio prov modifyCOS default zimbraPasswordMinPunctuationChars
carbonio prov modifyCOS default zimbraPasswordMinUpperCaseChars
carbonio prov modifyCOS default zimbraPasswordMinAlphaCharsIf a user tries to change a password to one that does not comply with the password policy, he will receive a corresponding warning explaining which rules of the password security policy his password violates.
Password policy settings for a user always take precedence over Class of Service settings. For example, if a minimum password length of 10 characters is specified at the COS level, and the settings of a user included in this Class of Service are 8 characters, then the user will be able to change the password containing 8 characters.
Another password security policy setting is how Carbonio behaves when a password is entered incorrectly. The administrator can configure both for an individual user and an entire Class of Service:
- Enable failed login blocking
- Number of valid consecutive failed entries
- Account lock time
- Time intervals with unsuccessful logins, after which the account is blocked
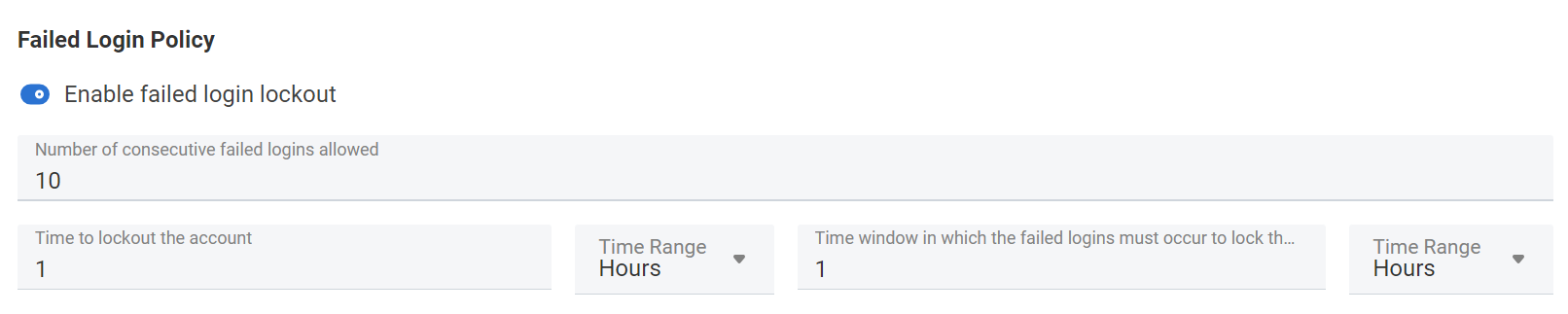
The same settings can be changed in the command line both at the individual user level and at the Class of Service level. At the user level, this is done using the following commands:
carbonio prov modifyAccount user@domain.tld zimbraPasswordLockoutEnabled
carbonio prov modifyAccount user@domain.tld zimbraPasswordLockoutMaxFailures
carbonio prov modifyAccount user@domain.tld zimbraPasswordLockoutDuration
carbonio prov modifyAccount user@domain.tld zimbraPasswordLockoutFailureLifetimeAt the COS level:
carbonio prov modifyCOS default zimbraPasswordLockoutEnabled
carbonio prov modifyCOS default zimbraPasswordLockoutMaxFailures
carbonio prov modifyCOS default zimbraPasswordLockoutDuration
carbonio prov modifyCOS default zimbraPasswordLockoutFailureLifetimeNote that although the idea of blocking accounts for unsuccessful login attempts is attractive from the point of view of increasing the security of the server and user data, in practice it is not recommended to use it. The main problem here is that attempts to change the password can occur without the knowledge of the user himself, which will lead to a situation where the user will not be able to work normally due to the fact that the attacker decided to brute force his account password. This is fraught with downtime and losses for the enterprise
Much more effective in this regard is protection against brute force using the Fail2ban utility, which bans not the account, but the attacker’s IP address for unsuccessful login attempts. Therefore, even during password brute force by an attacker, the account of the attacked user will remain operational.
You can install Fail2ban in Ubuntu 20.04 from the standard package manager sudo apt-get install fail2ban. After this, create a file /etc/fail2ban/filter.d/carbonio.conf and write the following regular expression in it:
[Definition]
failregex = \[ip=<HOST>;\] account - authentication failed for .* \(no such account\)$
\[ip=<HOST>;\] security - cmd=Auth; .* error=authentication failed for .*, invalid password;$
;oip=<HOST>;.* security - cmd=Auth; .* protocol=soap; error=authentication failed for .* invalid password;$
\[oip=<HOST>;.* SoapEngine - handler exception: authentication failed for .*, account not found$
WARN .*;ip=<HOST>;ua=CarbonioWebClient .* security - cmd=AdminAuth; .* error=authentication failed for .*;$
NOQUEUE: reject: RCPT from .*\[<HOST>\]: 550 5.1.1 .*: Recipient address rejected:Save your changes and edit the sudo nano /etc/fail2ban/jail.local file. Add the following rules for monitoring log files to it:
[carbonio-account]
enabled = true
filter = carbonio
action = iptables-allports[name=carbonio-account]
sendmail[name=carbonio-account, dest=zextras@example.tld]
logpath = /opt/zextras/log/mailbox.log
bantime = 600
maxretry = 5
[carbonio-audit]
enabled = true
filter = carbonio
action = iptables-allports[name=carbonio-audit]
sendmail[name=Carbonio-audit, dest=zextras@example.tld]
logpath = /opt/zextras/log/audit.log
bantime = 600
maxretry = 5
[carbonio-recipient]
enabled = true
filter = carbonio
action = iptables-allports[name=carbonio-recipient]
sendmail[name=Carbonio-recipient, dest=zextras@example.tld]
logpath = /var/log/carbonio.log
bantime = 172800
maxretry = 5
[postfix]
enabled = true
filter = postfix
action = iptables-multiport[name=postfix, port=smtp, protocol=tcp]
sendmail-buffered[name=Postfix, dest=zextras@example.tld]
logpath = /var/log/carbonio.log
bantime = 172800
maxretry = 5The changes we made are configured to monitor entries in the Carbonio logs and, if suspicious activity is detected, limit the offender’s access to the server by his IP address. Thus, when attempting brute force, it will not be the Carbonio account that will be banned, but the attacker who is trying to guess the password.
Save your changes and open the /etc/fail2ban/action.d/sendmail.conf file. In it, replace the line Fail2Ban" | /usr/sbin/sendmail -f <sender> <dest> with Fail2Ban" | /opt/zextras/common/sbin/sendmail -f <sender> <dest>.
Save the changes and restart Fail2ban for them to take effect
service fail2ban restartYou can check the fail2ban status using a command like
fail2ban-client status carbonio-auditIts output will display the number of times the rule was triggered and other information.
