Email security is one of the biggest concerns nowadays. Hacking users, infecting their computers with viruses and trojans, and sending millions of SPAM emails against the user’s will, all contribute to this concern. Authentication strategies such as user and password, Access Token, Security Assertion Markup Language, Two-Factor Authentication, Mobile Password, QR Code are always evolving, and knowing how to use and manage them will certainly help you to improve your Zimbra mailbox security. Zextras Auth tries to enable an administrator to apply and manage these strategies while it’s backward-compatible with Zimbra CustomAuth.
In general, the goal of the Zextras Auth can be summarized in improving the security via first, granting the user to manage multiple credentials and enable them for different services, and second, enabling the admins to define policies for each service, and give them more granular control over the user sessions.
To learn more about Zextras Auth, please refer to Zextras Auth Documentation.
What’s New
Zextras Suite 3.1.10 upgrades the Zextras Auth by adding support for Security Assertion Markup Language (SAML) and Two-Factor Authentication (2FA) to improve user security. Now let’s take a deeper look at these features.
What is SAML
Security Assertion Markup Language or SAML is an open standard for logging users into applications based on their sessions in another context. It means is that you can use one set of credentials to log in to many different platforms. It works by transferring the user’s identity data between two parties (from the identity provider or IdP to the service provider or SP). This is done via an exchange of digitally signed XML documents to authorize the users willing to use the Zimbra WebMail. SAML enables a Single-Sign-On or SSO which meant users can log in once, and those same credentials can be reused to log into other service providers.
What is 2FA
Two-factor authentication or 2FA is a method in which a user is granted access only after it successfully provides the authentication mechanism with two pieces of evidence like knowledge (something only the user knows, such as username and password), possession (something only the user has, such as a physical card, a mobile phone, or a security token), and inherence (something unique to the user, such as a fingerprint or other biometric trait). For example, an SMS-based 2FA uses the knowledge (username/password) and possession (such as a PIN). When both of these factors are required for authentication, makes it more difficult to bypass or hack.
In 2FA the device or the IP can be trusted. Trusting the device means that the next login from the same browser or mobile app will not ask for the second factor. Trusting the IP means that all the requests from the same IP for the same user will not ask for the second factor.
Why Are SAML and 2FA So Important?
Without SAML authentication the users should keep track of numerous usernames and passwords. This can lead to more forgotten passwords and cause less productivity and password fatigue for the users. Forgotten passwords on the other hand result in a lot of help desk tickets. On top of eliminating the annoyance of password fatigue for users, SAML authentication has several advantages over username/password login. For example, SAML can improve user experience since there is no need for the user to type the credentials and remember or renew the passwords. It can also increase security by providing a single point of authentication, and reduce costs for service providers since you don’t have to maintain account information across multiple services.
Two-factor authentication has several advantages over username/password login. For example, 2FA can improve security as it decreases the probability that an attacker can impersonate a user and gain access, even if a password is compromised, requiring the second factor of authentication is needed. It can also increase productivity by enabling the employees to securely access corporate applications, data, documents, and office systems from any device or location. 2FA will also reduce security costs by providing a safe and secure way for end-users to manage their own passwords and reduce the help desk technician’s time for security-related requests, tickets, and calls.
Zextras SAML Authentication
Zextras SAML authentication offers several powerful features that make it really easy for administrators to work with.
- Zextras SAML authentication is domain-based, which means it supports SAML at a single domain level, allowing different identity providers to be used for different domains (each domain can have a different SAML endpoint). If it was supported at the whole infrastructure level all systems must have used the same identity provider.
- Zextras SAML authentication coexists with standard authentication. Enabling it won’t prevent users from logging in with their username and password combination. Both SAML and standard authentication are available and users can easily choose between the two. When the feature is configured by the administrator for a domain, a button will be automatically available on the login page to log in using SAML.
- Zextras SAML authentication supports both Identity Provider Initiated and Service Provider Initiated SAML authentications. When it comes to SAML authentication, there are two schools of thought about where the identification starts. The web browser SSO profile can either start from the Identity Provider (IdP) or the Service Provider (SP), therefore they are respectively called IdP-initiated and SP-initiated SAML authentication methods.
- IdP-initiated SSO – In an IdP-initiated SSO, an unsolicited response element from the identity provider is sent to the service provider. In our case, the end-users should log into their identity provider account such as Okta, AzureAD, Auth0, UCS, etc., and click on a specific app to log into their Zimbra account.
- SP-initiated SSO – In an SP-initiated SSO, everything begins at the service provider which issues an authentication request to the identity provider. In our case, the end-users should use the LOGIN SAML button in the Zextras login page to send an authorization request to their identity provider such as Okta, when it’s approved they log into their Zimbra account.
What Administrators Should Know
Here we briefly go through some configurations an administrator should perform to use Zextras SAML authentication for a domain.
Zextras Suite Auth supports open standard on the SAML address https://domain.com/zx/auth/samlMetadata you will find an XML file with all the data that zextras as the SP sends to the IdP. There is a very similar XML file that is given by the Idp. Four pieces of information are copied from the XML file provided by the IdP, directly into the zextras configuration:
sp.assertion_consumer_service.url
idp.entityid
idp.single_sign_on_service.url
idp.x509certother parameters are optional.
The system administrators must upload the above-mentioned data for every domain they wish to enable. They can do that using a JSON file. They must create a text file and upload it via set and import commands
Example 1 – SAML configuration using Auth0
An administrator can configure the SAML authentication using their Auth0 console:
- Create an auth0 application
- set the endpoint to
ZimbraURL + /zx/auth/saml(https://infra-12345678.test.domain.com/zx/auth/saml) - enable Auth0 SAML2 addon
- insert the Application callback URL into the SAML setting
Customize AuthSAML setting:
{
"nameIdentifierFormat": "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress",
"nameIdentifierProbes": [
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"
]
}5. download the SAML metadata
In Zimbra
- !!!patch NGINX files!!!
- dump SAML config
> zxsuite auth saml get 12345678.test.domain.com export_to /tmp/saml.json- update JSON with
"sp.nameidformat":"urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress ",
"sp.entityid": >>ZimbraURL/zx/auth/samlMetadata?domain=UserDomain<<,
"sp.assertion_consumer_service.url": >>ZimbraURL/zx/auth/saml<<,
"idp.single_sign_on_service.url": >>SingleSignOnService<<,
"idp.entityid": >>EntityDescriptor<<,
"idp.x509cert": >>X509Certificate<<- import the configuration
zxsuite auth saml import 12345678.test.domain.com /tmp/saml.jsonExample 2 – SAML configuration using UCS
An administrator can configure the SAML authentication using their UCS console:
- Create a new SAML Identity Provider
- Set the Service Provider endpoint to
ZimbraURL + /zx/auth/samlMetadata(https://infra-12345678.test.domain.com/zx/auth/saml) - Set the
respondToZimbraURL + /zx/auth/saml - Set format of
NameIdAddresstourn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress - set the name of the attribute to
mailPrimaryAddress - download the SAML metadata
- add the IDP to the UCS User
In Zimbra
- !!!patch NGINX files!!!
- dump SAML config
> zxsuite auth saml get 12345678.test.domain.com export_to /tmp/saml.json- update JSON with
"sp.nameidformat":"urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress ",
"sp.entityid": >>ZimbraURL/zx/auth/samlMetadata?domain=UserDomain<<,
"sp.assertion_consumer_service.url": >>ZimbraURL/zx/auth/saml<<,
"idp.single_sign_on_service.url": >>SingleSignOnService<<,
"idp.entityid": >>EntityDescriptor<<,
"idp.x509cert": >>X509Certificate<<- import the configuration
zxsuite auth saml import 12345678.test.domain.com /tmp/saml.jsonExample 3 – SAML configuration using Okta
An administrator can configure the SAML authentication using their Okta console:
- Generate the Application insti the SAML IDP Section
- Set the
Single Sign On URLtoZimbraURL + /zx/auth/saml(https://infra-12345678.test.domain.com/zx/auth/saml) - Set the
AudiendURI toZimbraURL + /zx/auth/samlMetadata - Set
NameIdFormattoEmail Addressformat:emailAddress - download the SAML metadata
In Zimbra
- !!!patch NGINX files!!!
- dump SAML config
> zxsuite auth saml get 12345678.test.domain.com export_to /tmp/saml.json- update JSON with
"sp.nameidformat":"urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress ",
"sp.entityid": >>ZimbraURL/zx/auth/samlMetadata?domain=UserDomain<<,
"sp.assertion_consumer_service.url": >>ZimbraURL/zx/auth/saml<<,
"idp.single_sign_on_service.url": >>SingleSignOnService<<,
"idp.entityid": >>EntityDescriptor<<,
"idp.x509cert": >>X509Certificate<<- import the configuration
zxsuite auth saml import 12345678.test.domain.com /tmp/saml.jsonTo verify the SAML administration you can use
su zimbra
zxsuite auth saml get [address]Zextras 2FA authentication is managed via zxsuite auth token. This is an example of a session
zimbra_token_id 1050555587
user_id b2b0395d-b670-64d2-9873-01680b13ff37
expiration_timestamp Fri 02 Apr 2021 at 16:42:12
active true
id fa0204c3-e0dd-42de-ac1c-df1599b3cb8e
auditsp
protocol http
device_id daaacc322b908072
service_name MobileApp
ip_address 188.11.44.22
user_agent okhttp/4.9.0
successful true
timestamp 1617345732760
credential_id 6bBLcIn the end, you see the credential used.
The system administrators can set a range of IPs to indicate which IPs can be connected to a specific domain.
zxsuite auth policy set ZmWebUI domain {domain_name} ip_can_change true trusted_device 2 trusted_ip_range {ip_range}What end-users Should Know
Users can create a new user on Zextras and one or more SAMLs can be associated with the user by the administrator. Let’s take a quick look at two examples from a user’s point of view:
- In an IdP-initiated SSO, I as a user access my Okta account (my IdP), I log in if prompted, then click the designated app to direct me to my Zimbra account without the need to provide my Zimbra account credentials.
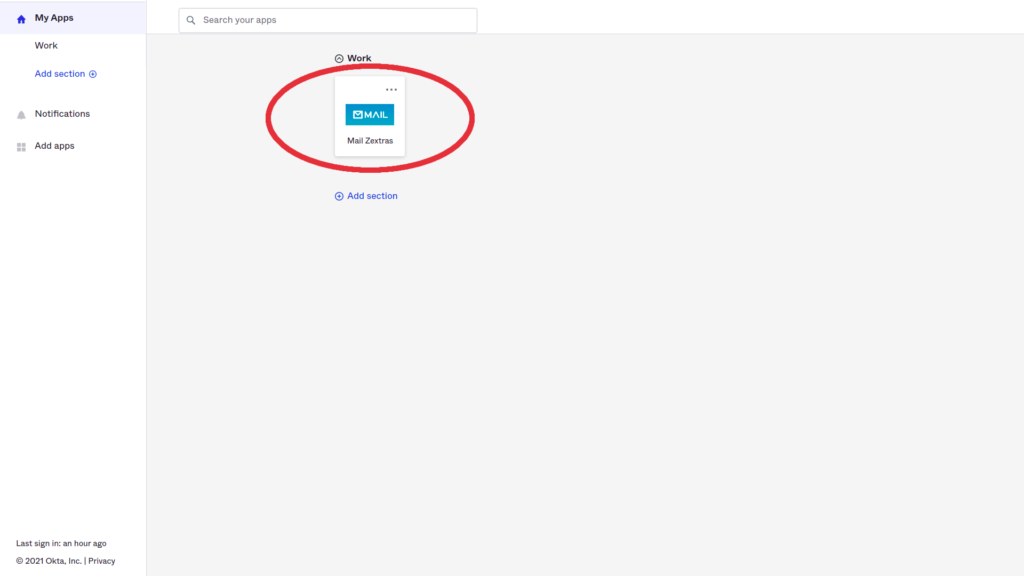
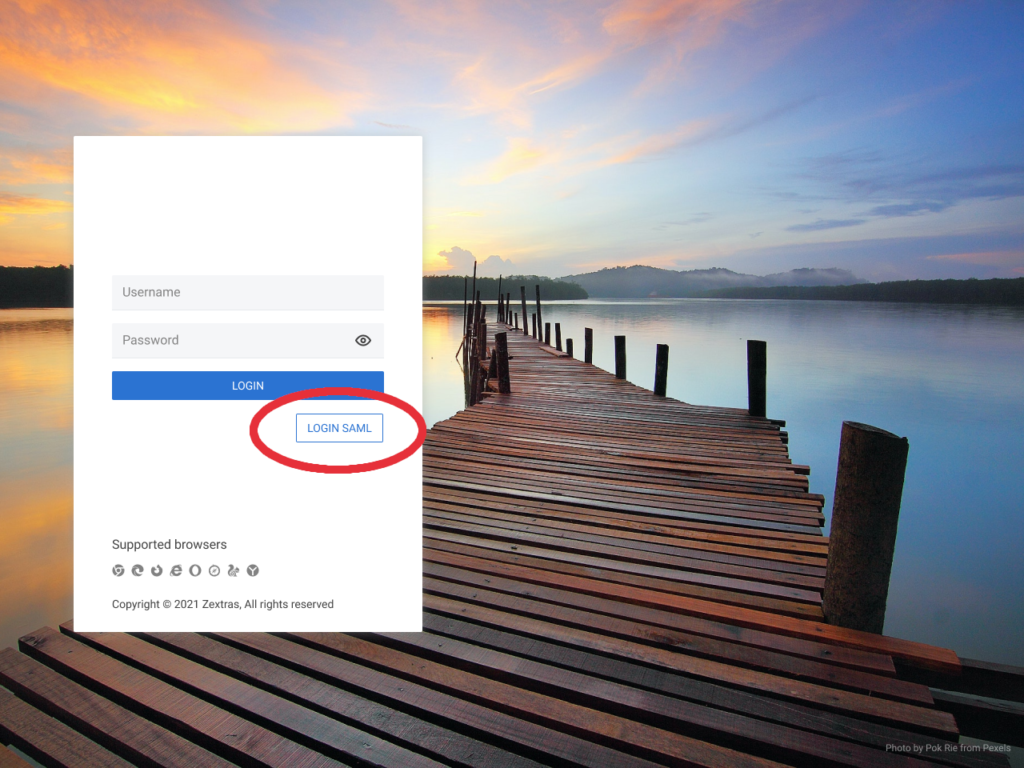
- In an SP-initiated SSO, I as a user go on the Zextras login page (my SP) and click the LOGIN SAML button, I will be redirected to my Okta account (my IdP), then I log in if prompted, and then I’m authenticated to my Zimbra account without the need to provide my Zimbra account credentials.
How users can access their account using SAML
The users can access their account using SAML:
- Click the LOGIN SAML button on the login page,
- If prompted, log into your IdP account (in this case Okta)
- You will be directed to your Zimbra account with no need to insert your Zimbra username and password.
Alternatively, you can,
- Log into your IdP account (in this case Okta),
- Select Mail Zextras app to be directed to your Zextras account.

How users can access their account using 2FA
To use the 2FA feature users need to create a new one-time password (OTP) as follows:
How to Create an OTP for 2FA
- Log into your account on Zimbra Web Client,
- Select the Zextras Auth under the Zimlets pane on the left,

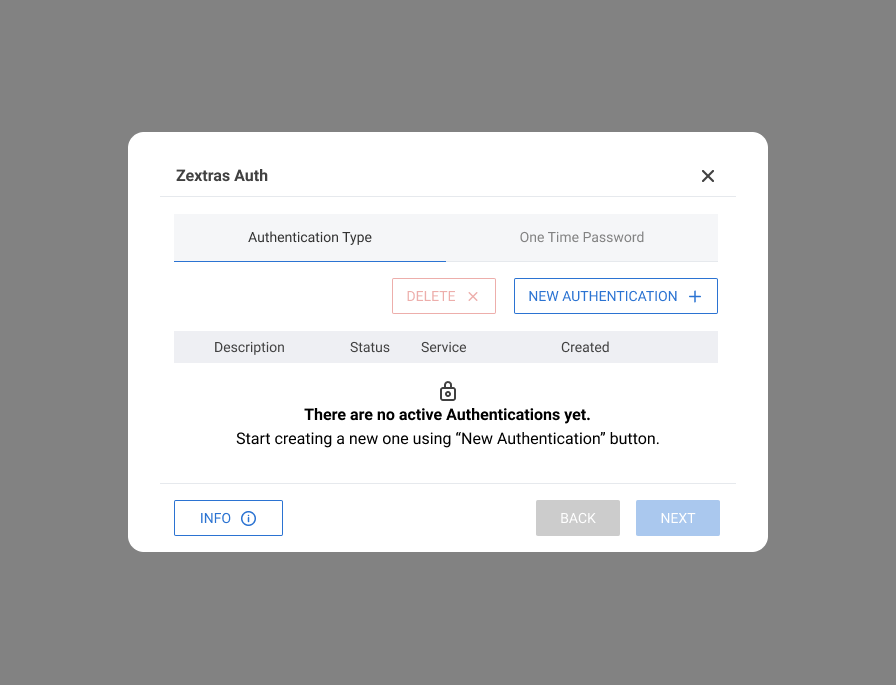
Click on the One Time Password tab
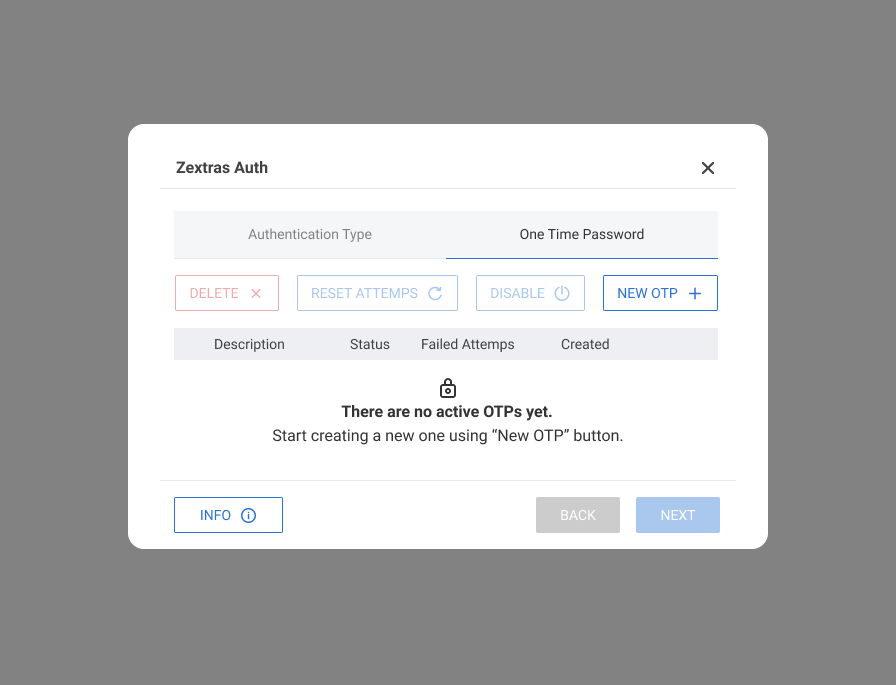
Click the New OTP + button,
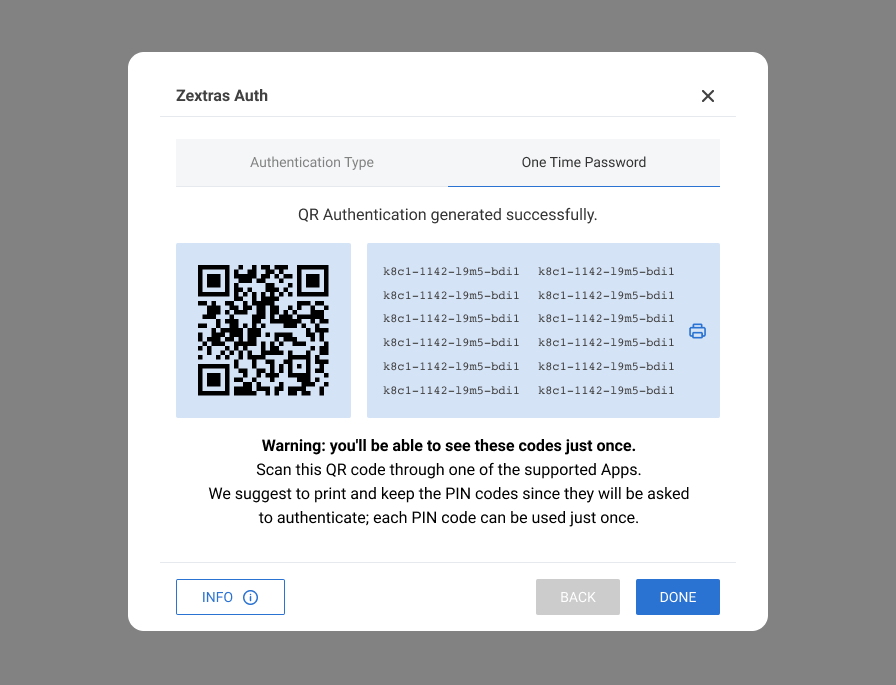
- Add the OTPs to the Google Authenticator app on your mobile device by scanning the generated QR code, you can also use other tOTP supported apps,
- Optionally you can click the print button to save the OTPs in a secure location,
- Click Done to see the new password in the list
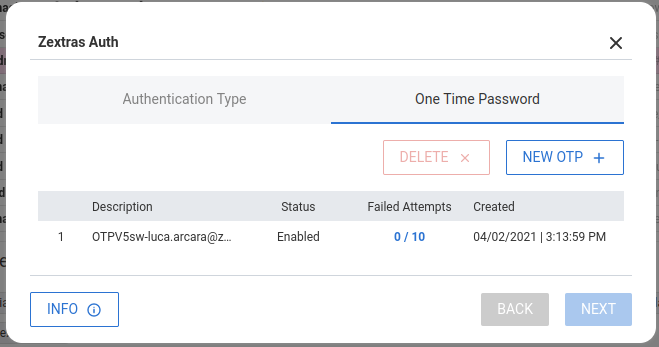
Once users create an OTP they can access their account using 2FA as follows:
If 2FA is enabled for a domain, next time users try to sign in to their account, they will be asked to provide the 2FA credentials in addition to their username and password. To do so:
- Insert your username and password as usual on the login page,
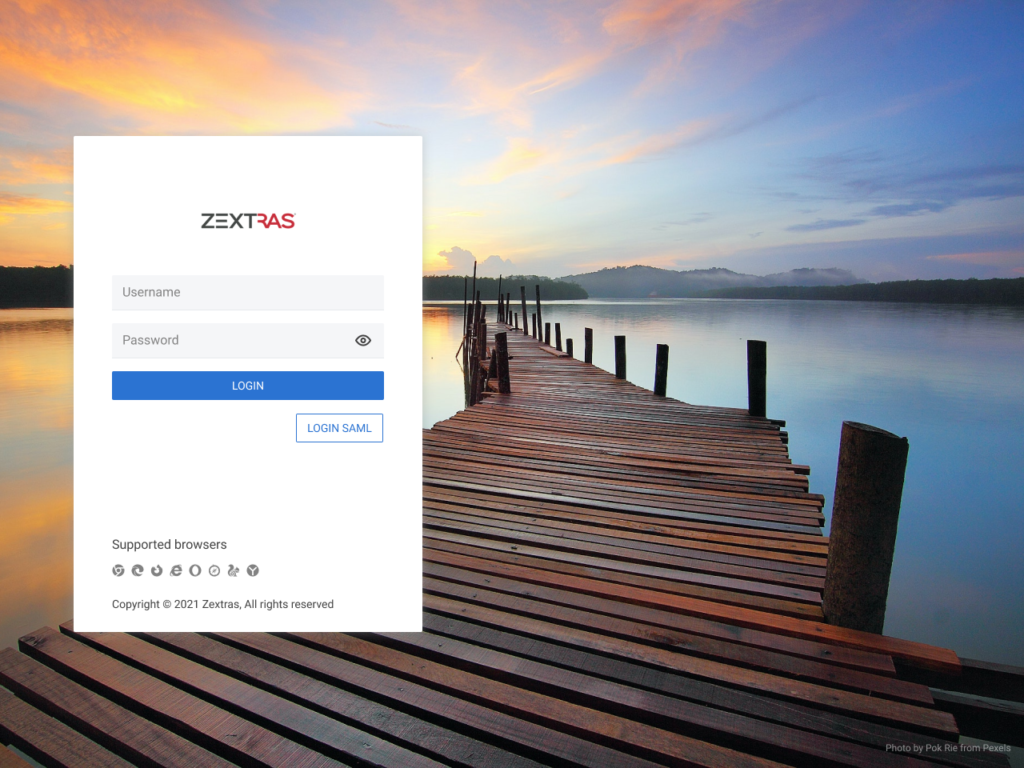
- Click the LOGIN button,
- You will be asked to insert your Two-Step-Authentication credentials,
- On the login page, insert the code provided by Google Authenticator app on your mobile device,
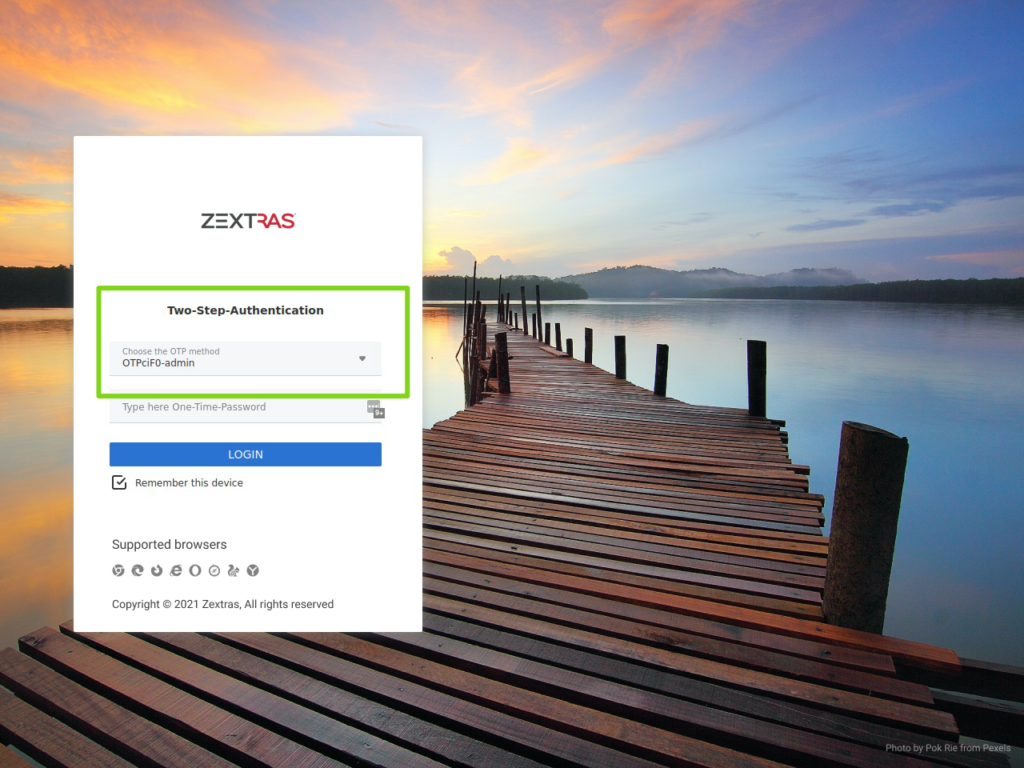
Click the LOGIN button.
