In this article, we will discuss one of the main e-mail protection strategies: SPF, and show you how to implement it on your Carbonio CE servers properly. We will follow this with more articles about other common e-mail protection strategies.
What is SPF?
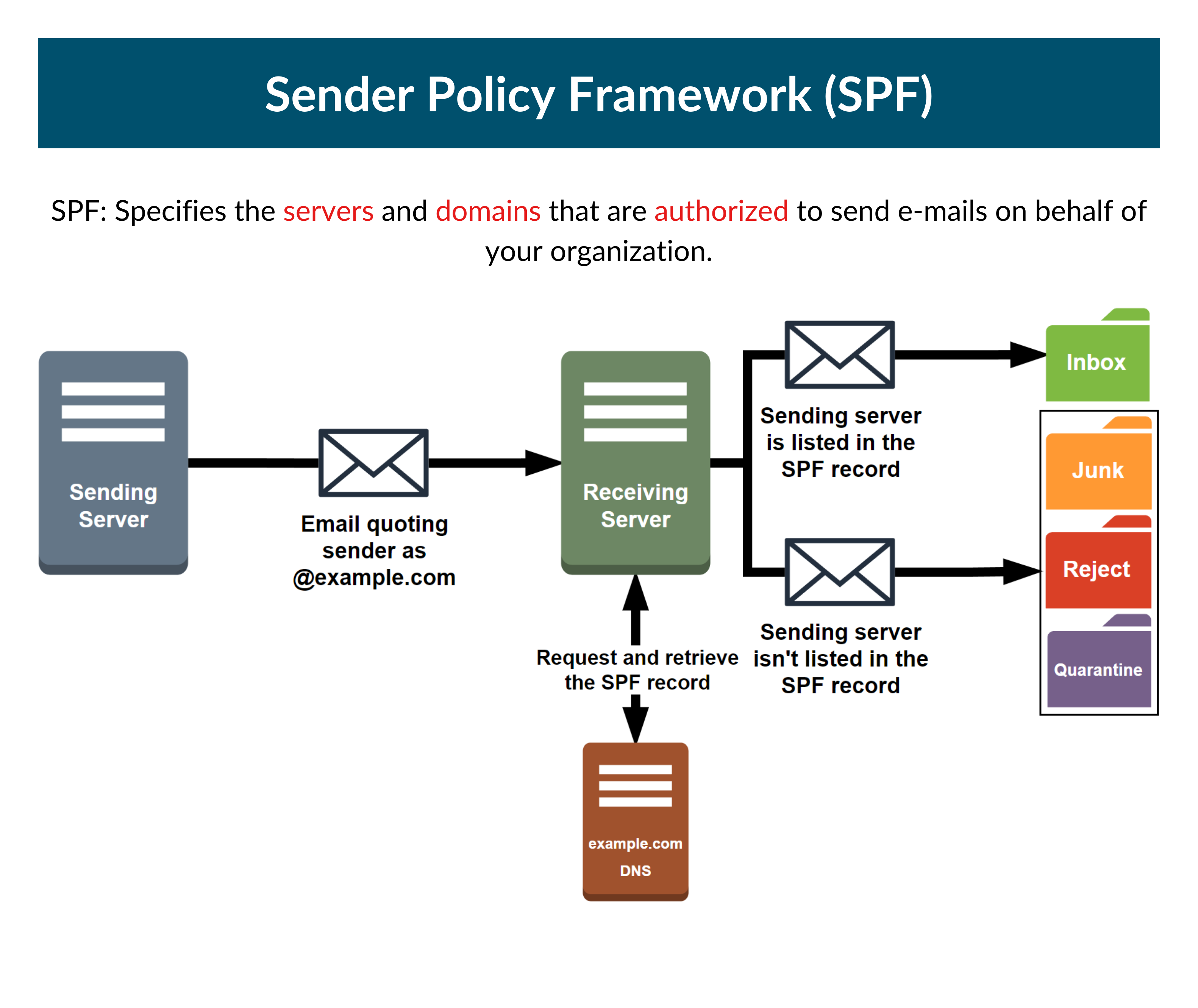
The Sender Policy Framework (SPF) is a phishing-prevention e-mail authentication mechanism. It allows your company to choose who is permitted to send e-mails on your domain’s behalf. This is important because, in a typical phishing attack, the threat actor spoofs the sender’s address to look to be an official corporate account or someone the victim knows.
Note: SPF does not prevent spoofing of the “header from” address that users see in their e-mail clients. SPF may be bypassed by adding a domain owned by the criminal in the “envelope from” address while spoofing a legal brand’s domain in the visible from address.
Why Is SPF Important?
SPF is a DNS TXT record that determines which IP addresses and/or servers may send e-mails “from” a specific domain. It’s similar to the return address on a letter or postcard, which informs the recipient of who provided the information. The notion is that if the receiver knows who sent them the letter, they are more inclined to open it. However, in this case, the receiver is the receiving mail server, as opposed to the person being e-mailed.
Moreover, because SPF makes it more difficult for cybercriminals to fake your domain, spam filters are less likely to ban it. Your genuine e-mail’s deliverability improves as a result of this better reputation. If you do not have an SPF record, the recipient’s e-mail server may notify them that the message may be from a phishing attacker. Some corporate e-mail servers delete messages or route them directly to the receiver’s spam mailbox, so the recipient may never get them.
Outgoing vs. Incoming E-mails
Like DKIM, SPF can be configured both for incoming e-mails and outgoing e-mails. This is while system administrators usually refer to configuring SPF for the outgoing messages when talking about SPF.
Configuring SPF for the outgoing e-mails protects your reputation while configuring SPF for your incoming e-mail would protect your user’s information. Because they serve different purposes, a system administrator must equip the servers with both functions. We’ll go through how to enable both techniques further down.
Let’s start with the incoming e-mails.
How to Configure SPF for Incoming E-mails in Carbonio CE
As we said, it is possible to configure SPF validation on the Carbonio servers to protect your servers and users’ information against unwanted e-mails. By configuring SPF for incoming e-mails, you can automatically reject incoming e-mails from sources with no SPF record.
We utilize the CBPolicyD WebUI to establish a new policy to enable SPF to verify incoming e-mails. Follow these steps to establish a new policy:
- Create Group
- Select Policies | Groups.
- From Action, select add a group with the name list_domain.
- Select the new group.
- From Action, select members and insert your domain.
- Create Policy
- Select Policies | Main.
- Add Policy with the Name check-spf and Priority 20 and Submit.
- Select the new policy.
- From Action, select members and insert our group name in the Source and Destination.
- Create SPF Check
- Select SPF Checks | Configure.
- From Action, select Add and set the Name and Link to policy to check-spf, and others to Yes and Submit.
- Enable CBPolicyD
checkspfand restart the server.
How to Configure SPF for Outgoing E-mails in Carbonio CE
SPF for outgoing e-mail increases the trustworthiness of communications sent by users on your servers. This occurs when the receiving server recognized the SPF record configured on your server.
To do so, you simply
- Create your SPF record
- Add your SPF record to the DNS
Below you will find the detailed instruction.
Step 1: Create Your SPF Record
- Firstly, we define the SPF version, for example, v=spf1 for version 1.
- Then add all IP addresses that are authorized to send e-mails on your behalf, for example,
v=spf1 ip4:34.243.61.237 ip6:2a05:d018:e3:8c00:bb71:dea8:8b83:851e - Use the
includetag for every third-party organization that is used to send e-mails on your behalf, likeinclude:thirdpartydomain.com, alternatively, ignore theincludetag if there is no third-party organization. - End the record with an
~all,-all, or+alltag. The -all tag means fail (servers that aren’t listed in the SPF record are not authorized to send e-mails). The ~all means soft fail (If the e-mail is received from a server that isn’t listed, the e-mail be accepted but marked), the+allallows any server to send e-mail from your domain (which should never be used).- For example, if you want only your cloud server (incoming mail exchange (MX)) and no other mail servers to be authorized your rule would be
v=spf1 mx -all, if you wish your cloud server and Microsoft Exchange Online mail server but no other mail servers to be authorized your rule would bev=spf1 include:spf.protection.outlook.com -all. If you are using external services like Mailchimp, Salesforce, Google Apps, etc. add them in the include part, for example,include:servers.mcsv.netfor Mailchimp,include:_spf.salesforce.comfor Salesforceinclude:_spf.google.comfor Google Apps.
- For example, if you want only your cloud server (incoming mail exchange (MX)) and no other mail servers to be authorized your rule would be
sudo apt-get install libxml-simple-perlAfter the package is installed on into your zextras account and run the script
Step 2: Add Your SPF Rule to the DNS
Now it’s time to add the SPF record created in the previous section to your DNS. To do so
- Access your DNS provider, for example, GoDaddy, Network Solutions, etc.
- Access your DNS Management based on your provider it can be something like name server management.
- Add a new TXT entry setting
Record Typeas TXT. - Insert @ in the
Hostnamefield to map the record directly to your domain name. - Insert the created SPF rule in the
TXT Valuefield. - Assign the Time to Live (TTL), for example, let’s use 3600s.
- Save the entry.
Testing it All Out
Assume you’ve already generated your SPF rule, added it to your DNS, and want to double-check its setup. The SPF record is kept in DNS as TXT, and you may manually verify it for a domain using nslookup or dig, as shown below.
nslookup -type=txt domainor
dig txt domainReplace domain with your domain name, for example, nslookup -type=txt example.com,
These tools look for your SPF record to be present, if so you will see your record as v=spf1 ..., otherwise, there is an issue with obtaining the record, not showing v=spf1.
Alternatively, to test your SPF, insert your domain into https://mxtoolbox.com/spf.aspx and see if the DNS entry for your SPF is valid. If your DNS entry is properly configured, it will display the results, indicating that your SPF passed the test. The MX toolbox should be sufficient to test your SPF, although there are additional tools accessible online for this purpose. http://tools.wordtothewise.com/spf is another tool you may use to see a list of IPs you designated as approved in your SPF rule. You may also use http://www.kitterman.com/spf/validate.html to check the DNS entry for your SPF.
You may also send an e-mail to Gmail to test if your e-mail contains the mailed-by entry on e-mail information, which indicates that Google has successfully detected your e-mail SPF setup.
