For additional guidance, check out our community articles detailing the process of migrating from your current platform to Carbonio CE.
For enterprise-level requirements and advanced features, consider checking out Zextras Carbonio – the all-in-one private digital workplace designed for digital sovereignty trusted by the public sector, telcos, and regulated industries.
Security is not an option.

Unfortunately, many companies meet security only after an attack has been received, or when they have to limit the damages of a data breach.
Security is not only about c0mpl3x and very-long-but-hard-to-remember passwords. Complex password works against brute force or dictionary attack, but they cannot help in case of phishing, social engineering, or, more frequent, un-secure “storage” (ops, Have I to trash my post-it?)
Fight against this kind of attack requires trust more than complexity. Users must trusts who is asking for their credentials. Systems must trust who is asking for a login.
How to create this trusted environment and help sysadmin to protect their server and user to protect themselves?
One approach is the “Second Factor”. Basically, the user has something both he and the system know (typically username and password) and something that only the user knows (typically a temporary code or a physical device). Even if one of the factors is compromised, the unauthorized connection cannot be trusted without the second factor.
2FA sounds the best option, but it’s also really annoying for the user, that has to type the second factor each time.
For this reason, Zextras Auth introduced the “trusted connection“. If the connection came from a defined IPs’ range or from a Trusted device, access is granted, otherwise, a second factor is required.
Zextras Auth allows admin to manage scenario like the following:
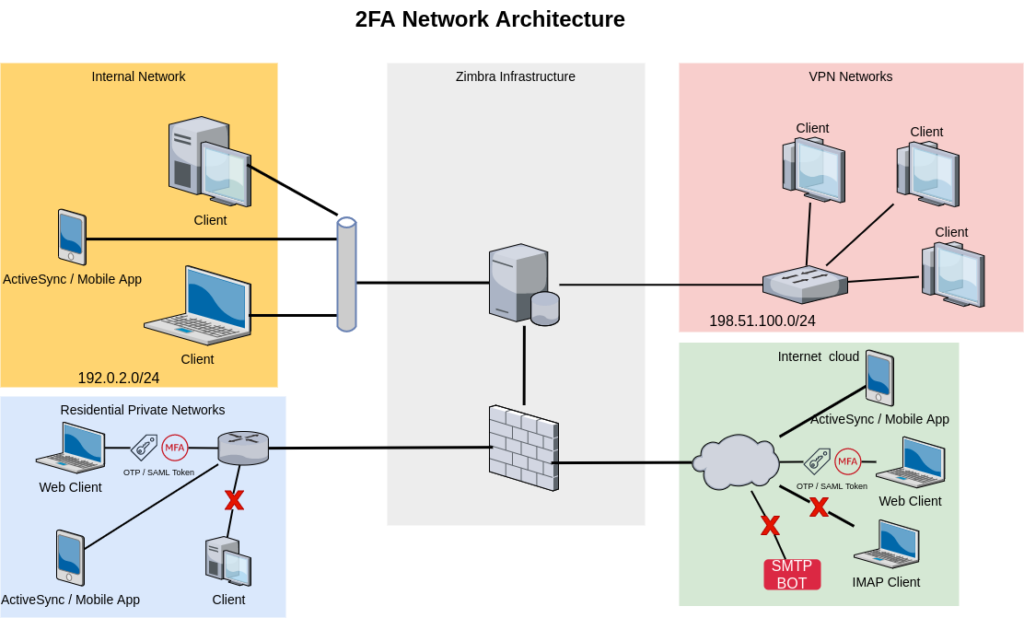
Admin wants users from the Internal Network and VPN access the infrastructure without any additional request for security or One Time Password.
At the same time, he wants users working from their homes to access Zimbra services in a more secure way, to avoid phishing and brute force attack. And he also would like that ActiveSync and Mobile App are available everywhere.
Using Zextras Auth, our admin can configure the Authentication service to:
- trust any connection from internal IPs (192.0.2.0/24, 198.51.100.0/24, and infrastructure IPs). Clients from this network will not ask for any additional factor
- use the EAS Mobile Password to allow ActiveSync for any device from any network. MobilePassword cannot be used to access other services rather than the ActiveSync
- Outside the trusted network, users can only access the WebMail using 2FA with OTP or a SAML Token
Moreover, all these configurations are available at domain-level, allowing Admin (and ISP) to provide more complex scenarios.
Another feature of the Zextras auth is the domain-based SAML authentication.
For example, consider an ISP that wants to provide a different security model for its customer.
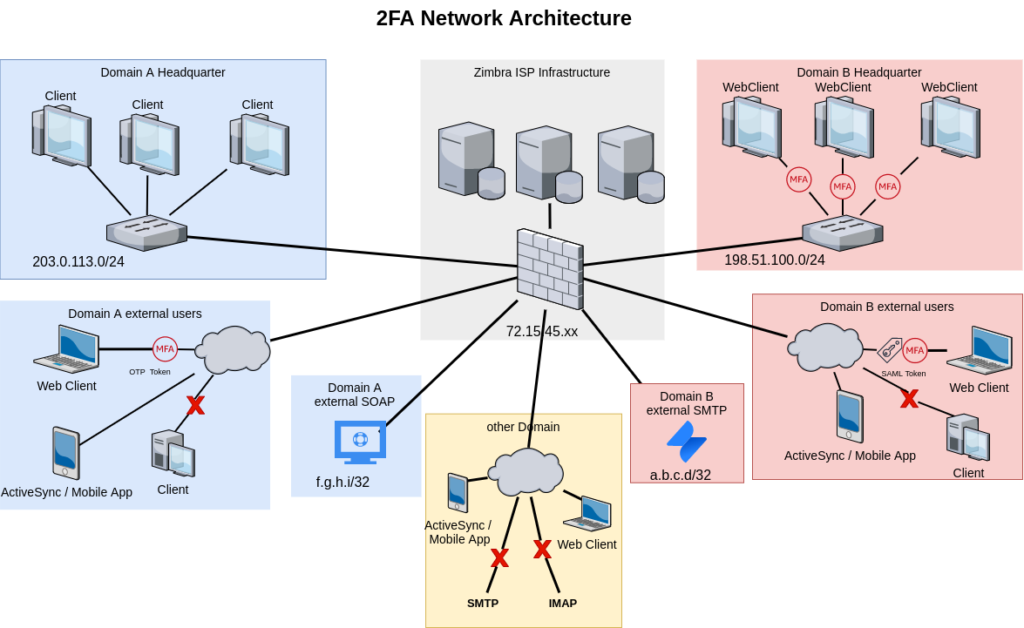
admin@a.tld wants his users to be able to work from the company office in the easiest way, but at the same time he wants users connecting from outside the internal LAN to be able only to use WebClient with the second factor and he doesn’t want SMTP or other protocols to be available outside their network. Whit one exception for the help desk service they bought that has to use the Zimbra SOAP call.
admin@b.tld wants high-level security, avoiding any usage of SMTP or IMAP. He wants to allow only web client access authorized by 2FA or SAML, either from the internal or the external network. With only one exception for the external service they are using, that requires a valid SMTP authentication.
All accounts from other domains can use only the WebClient and ActiveSync protocol.
An awesome feature of Zextras auth is the ability to trust either the Device or the IP.
With the IP-based trust, also services and protocols that don’t support the 2FA could become accessible outside the trusted network.
For example, an admin that wants to allow SMTP and IMAP from the user’s home IP can configure the domain auth to allow the user to
- authenticate to the WebClient using the OTP
- add the home IP to the trust IPs
- use the SMTP or the IMAP from a trusted connection
- once the trust is expired, the user needs to re-authenticate with the WebClient
Zextras Auth makes authentication stronger and more flexible, allowing admin to easily adapts the authentication strategies to their needs, and not adapting the user experience to the product need.
In conclusion, some tips to obtain the maximum for your Zextras Auth
- use single factor auth only from a really trusted connection
- if you want the user to be able to trust his current IP, reduce the default expiration, for example to 1 or 2 days.
- Never store, reuse or share the Active Sync password.
- To strictly limit services, use the loopback or the infrastructure Ips as trusted IP range


Comments
Great article, Luca!!